In today’s digital age, cybersecurity threats are becoming increasingly common and sophisticated. One of the most common forms of cyber-attacks is ransomware, which involves cyber criminals taking control of an individual or organization’s computer system and demanding a ransom to restore it.

Lawyers are among the most vulnerable professionals when it comes to ransomware attacks. They deal with sensitive client data and confidential information that can be exploited by cyber criminals. The consequences of a successful ransomware attack on a law firm can be disastrous, ranging from financial loss, reputational damage, and compromised data. Securing themselves from such attacks is essential for lawyers to ensure that their clients’ information remains confidential and secure.
While there are various ways cyber criminals can gain access to a system, one of the most common is through compromised credentials. It is, therefore, essential for individuals and organizations to prioritize protecting their login credentials to minimize the risk of ransomware attacks.
Compromised credentials refer to login information such as usernames and passwords that have been stolen or obtained by cyber criminals through various methods such as phishing or brute-force attacks. Cyber criminals can then use these credentials to gain unauthorized access to a system and introduce malware that can cause significant damage. In this blog post, we will delve into the specifics of how compromised credentials lead to ransomware attacks and discuss some practical steps that individuals and organizations can take to protect their login credentials.
1. Why Lawyers need to secure themselves from Ransomware attacks?
Lawyers are tasked with handling confidential and sensitive information on a daily basis, making them prime targets for ransomware attacks. Ransomware is a type of malicious software that encrypts files and demands payment in exchange for the decryption key.
The consequences of a successful ransomware attack on a law firm can be devastating, including the loss of critical data, damage to the firm’s reputation, and potential legal and financial liabilities. It is crucial for lawyers to take proactive measures to secure their systems against ransomware attacks, such as implementing strong cybersecurity policies, regularly backing up data etc. Failure to do so could result in significant harm to the firm and its clients.
2. Identifying the risk of credential-based ransomware attacks
One of the most common causes of ransomware attacks is the use of compromised credentials. Attackers often leverage stolen login credentials, such as usernames and passwords, to gain unauthorized access to systems and networks. Once they gain access, they can deploy their ransomware to lock out legitimate users and demand a ransom payment.
Organizations need to identify the risk of credential-based ransomware attacks and take steps to mitigate that risk. This includes implementing strong access controls, such as multi-factor authentication, to prevent unauthorized access to systems. It also involves regularly monitoring access logs and auditing user activity to detect and respond to suspicious behavior.
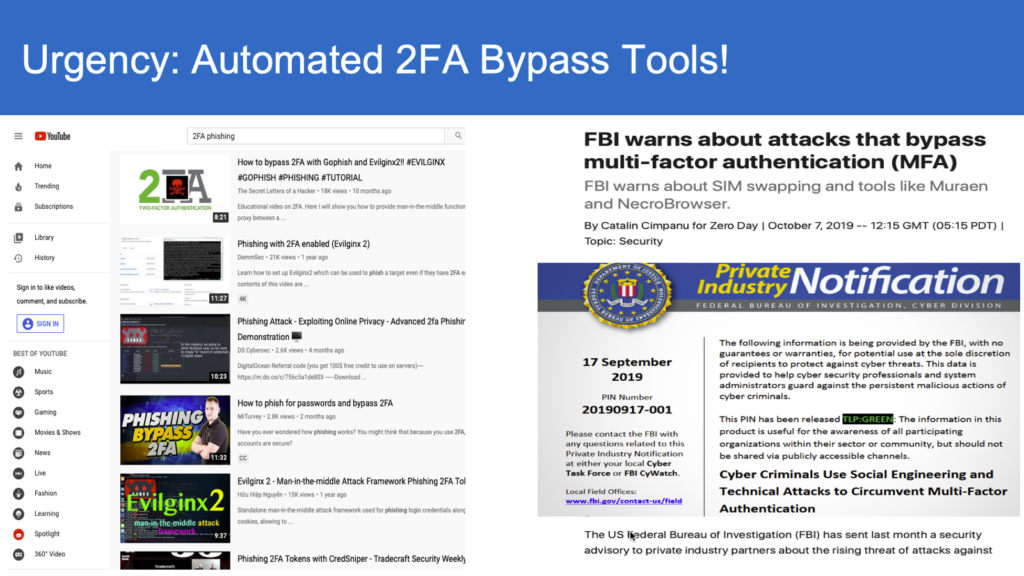
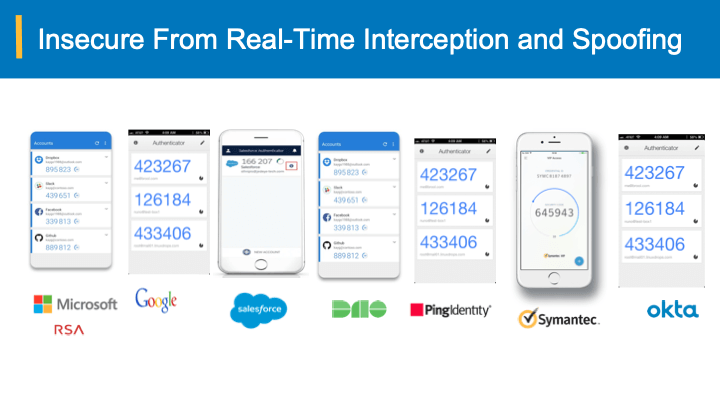
While cyber security pundits have been advocating the use of strong passwords and multifactor authentication, the hackers have leveled up the game with “multi-factor bypass” and real time interception of login credentials through malicious proxy servers. As we described here, the root cause is the ownership-agnostic bearer passwords, one-time codes etc. that when intercepted, stolen or hacked can be submitted by any one including hackers.
Taking proactive steps to address the risk of credential-based ransomware attacks is essential for organizations to protect their data and systems from unauthorized access and the often-devastating consequences of a successful attack. One such method is adopt bearer-sensitive login process that is simple and yet powerful to detect interception, spoofed and bypassed credentials and yet easily secure your online accounts.
3. How ransomware attacks progress from compromised credentials
One of the many ways ransomware attacks are initiated is through the exploitation of compromised credentials. Often, attackers will use tactics such as phishing or social engineering to obtain legitimate login credentials to gain access to a victim’s systems. Once they have successfully accessed a system using legitimate login credentials, they can move laterally within the network and escalate privileges to seek out critical systems, such as those that store sensitive data or hold vital infrastructure. Once these systems are compromised, the ransomware can be deployed, encrypting the victim’s data and demanding payment in exchange for the decryption key.
Therefore, it is strongly recommended to adopt bearer-sensitive multi-factor authentication, regular security training, and ongoing monitoring of all authenticated user activity.
4. Making user credentials use-less for hackers?
Compromised user credentials are responsible for a significant portion of successful ransomware attacks. According to cybersecurity reports, a staggering 80% of data breaches occur due to weak or stolen passwords, which allow attackers to gain unauthorized access to sensitive corporate information.
Bearer-aware credentials are typically generated from both intrinsic and extrinsic attributes that are observable on the login devices and environment. The bearer-aware credentials are often realized as one-time codes, but special algorithms run behind the scenes, taking into account such attributes. This, in essence, ties the ownership back to the trusted devices on which the user is logging in. A remote hacker or proxy server has different intrinsic and extrinsic attributes inherent to their system, and these can be observed by a bearer-aware authentication system; the cyber criminal cannot mimic nor impersonate the bearer-aware credentials through interception.
Law firms using bearer-aware authentication codes are now free to focus on the practice of law rather than worrying about their credentials falling in to wrong hands and the impact of a breach.
5. Keeping up to date with security patches
One critical measure in preventing ransomware attacks resulting from compromised credentials is keeping up to date with security patches. Software vendors often release security patches and updates to address security vulnerabilities and improve system performance. Failing to apply these patches and updates in a timely manner can expose your systems to exploitation by attackers and lead to devastating consequences. Ransomware attackers are known to exploit unpatched vulnerabilities and gain access to systems, where they deploy their malicious payloads, encrypting files and demanding ransom payment. Regular updates and patches to operating systems, firmware, and software applications should be prioritized as a priority to prevent unauthorized access and reduce the risk of ransomware attacks. Cyber criminals are constantly evolving their tactics, and updating systems on a regular basis is an important aspect of maintaining a strong security posture and protecting against the latest threats.
To conclude, as the digital world grows rapidly, cyber threats continue to become more sophisticated and dangerous. The exploitation of compromised credentials is a prime example of a threat targeting the heart of the IT infrastructure. Therefore, businesses and individuals should adopt robust security measures, including multi-factor authentication and regular password changes, to prevent the abuse of compromised credentials for ransomware attacks. As the saying goes, prevention is better than cure, and this has never been more true in the case of cybersecurity. Being proactive and vigilant in protecting your information can save you from expensive and devastating cyber attacks in the future.