I am not a technical geek; Explain what is iLogSafe that I can understand?
Can you pass on passwords and OTPs to hackers and still feel secure? Obviously “No”. With iLogsafe, even when hackers get your codes, your accounts are secured. Your exclusive iLogSafe codes are useless for hackers, providing a password-less hassle-free secure login.
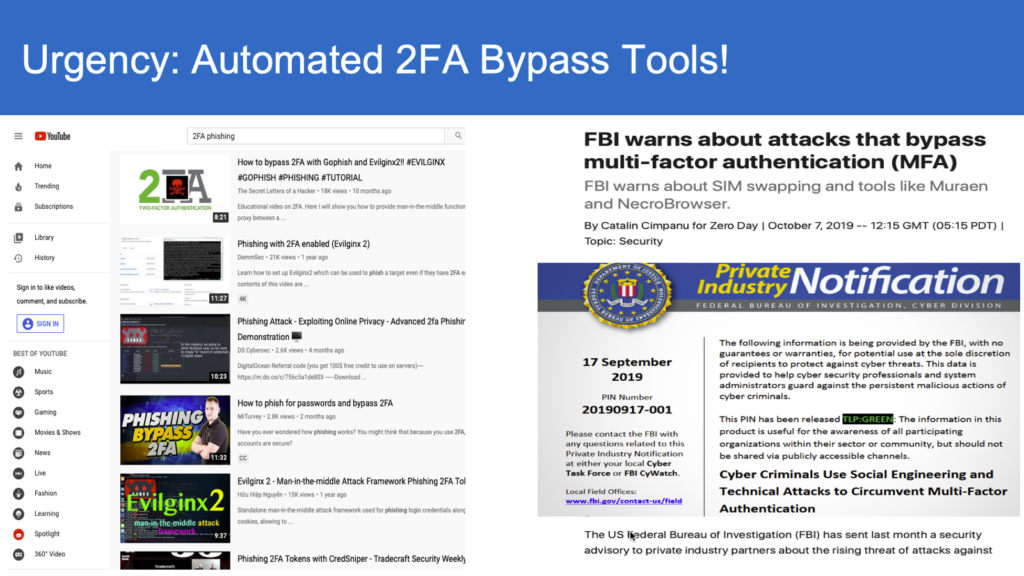
Can you show the details of how my 2FA is vulnerable(contains hacker demo videos)?
The recent attacks as documented by Microsoft on more than 10K enterprises can be easily addressed by iLogSafe and for details please go Here
Below video demonstrates how push notification authentication/approval 2FA can be compromised.
Watch below video on how OTP 2FA can be compromised.
Disclaimer: *copyrights belong to breakdev.org
Below video demonstrates how push notification authentication/approval 2FA can be compromised.
Watch below video on how OTP 2FA can be compromised.
Disclaimer: *copyrights belong to breakdev.org
I use faceId and Voice along with fingerprint and approvals on the app. Am I not secured?
The bio-metrics have been the mainstream when it comes to authenticating to the gadgets in our possession. But when it comes to online authentication, such authentication schemes fail to secure you from man-in-middle attacks as shown in the “app-based approvals” video.
Disclaimer: *copyrights belong to breakdev.org
Disclaimer: *copyrights belong to breakdev.org
I use super strong passwords, OTPs? Why do I need iLogSafe?
Passwords and OTPs were good until yesterday. With real-time interception and hacking (spoofing) your passwords and OTPs are now more vulnerable. Don’t take our word, following reinforce the fact that they are no longer secure.


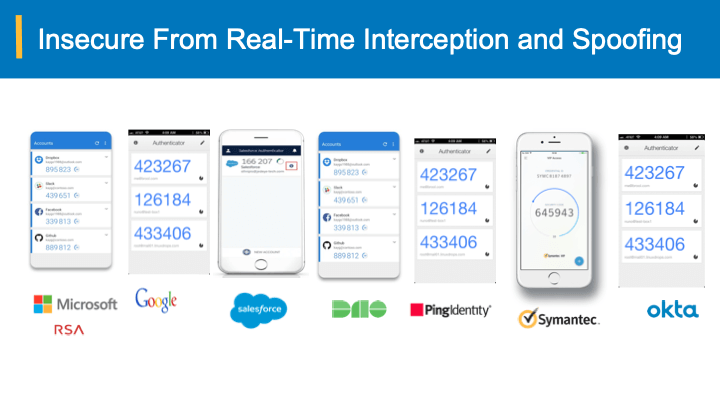
I use public and private keys; am I not secure?
Yes, public and private key pairs are secure than passwords. However mobility across devices with keychains and webauthn are clunky at best with so many variant offerings. One can always replace public key and replace real user permanently;Read our article for more details HERE
How does iLogSafe secure my online accounts, money from hackers?
iLogSafe provides a frictionless and easy to use login codes that are locked up to your devices. The patented technology will enable detection of spoofing when someone else intercepts and submits codes. We are an industry standard and meet NIST AAL-3, which means your money and online accounts are hacker-safe.
If you are serious about securing your money and accounts from fraudsters, signup now for great early bird discounts (more than $150 value package)
If you are serious about securing your money and accounts from fraudsters, signup now for great early bird discounts (more than $150 value package)
Do I need to create another set of passwords etc.?
No. We are passwordless.
We don’t use any of your sensitive information such as biometrics nor any private information, including your cell phone details.
Our patented technology is fun to use and intuitive to understand. No teasing of your brain memory nor we ask to solve hair-pulling puzzles.
Your grandma can use this once the account is setup!
We don’t use any of your sensitive information such as biometrics nor any private information, including your cell phone details.
Our patented technology is fun to use and intuitive to understand. No teasing of your brain memory nor we ask to solve hair-pulling puzzles.
Your grandma can use this once the account is setup!
I got many more SaaS applications, can you secure them all?
Absolutely!
Below is a starter list. If your SaaS application is not in this list please fill out here
Our product team will work towards securing that app with iLogSafe.

Below is a starter list. If your SaaS application is not in this list please fill out here
Our product team will work towards securing that app with iLogSafe.

Do I need to create multiple iLogSafe accounts for all the SaaS applications I need to protect?
No. One iLogSafe account can secure everything with our industry standard single-sign on and federation ; completely transparent to you and you just keep using your iLogSafe account.
What is the genesis of iLogSafe? Has this been tested?
iLogSafe is the culmination of years of hacking experience and cyber security management. Patents have been issued as a testimonial of the novelty and the utility of this unique technology pioneered by iLogSafe.
Easy to use and verify its security properties even by non-technical persons, scalable solution designed by a Ph.D. in computer science with CISSP/CISM certification, a regular speaker/presentor at several security conferences and who has successfully run Fortune 500 information security and risk management programs.
At the same time, even with such extensive information security expertise with iLogSafe team, we don’t relax; we are constantly plugged into latest cyber threats and move our program roadmap taking the latest hacks into account.
Our systems are constantly tested by real hacking from our pen-testing team and it goes through multiple checks on OWASP 10, Open API security standards through static and dynamic scans/testing.
Easy to use and verify its security properties even by non-technical persons, scalable solution designed by a Ph.D. in computer science with CISSP/CISM certification, a regular speaker/presentor at several security conferences and who has successfully run Fortune 500 information security and risk management programs.
At the same time, even with such extensive information security expertise with iLogSafe team, we don’t relax; we are constantly plugged into latest cyber threats and move our program roadmap taking the latest hacks into account.
Our systems are constantly tested by real hacking from our pen-testing team and it goes through multiple checks on OWASP 10, Open API security standards through static and dynamic scans/testing.
Any official articles that talk about this?
Yes, here is link of featured article at ‘American Bar Association’
https://www.americanbar.org/groups/gpsolo/publications/gpsolo_ereport/2022/october-2022/multi-factor-bypass-attacks-how-protect-your-law-firms-data/
https://www.americanbar.org/groups/gpsolo/publications/gpsolo_ereport/2022/october-2022/multi-factor-bypass-attacks-how-protect-your-law-firms-data/

