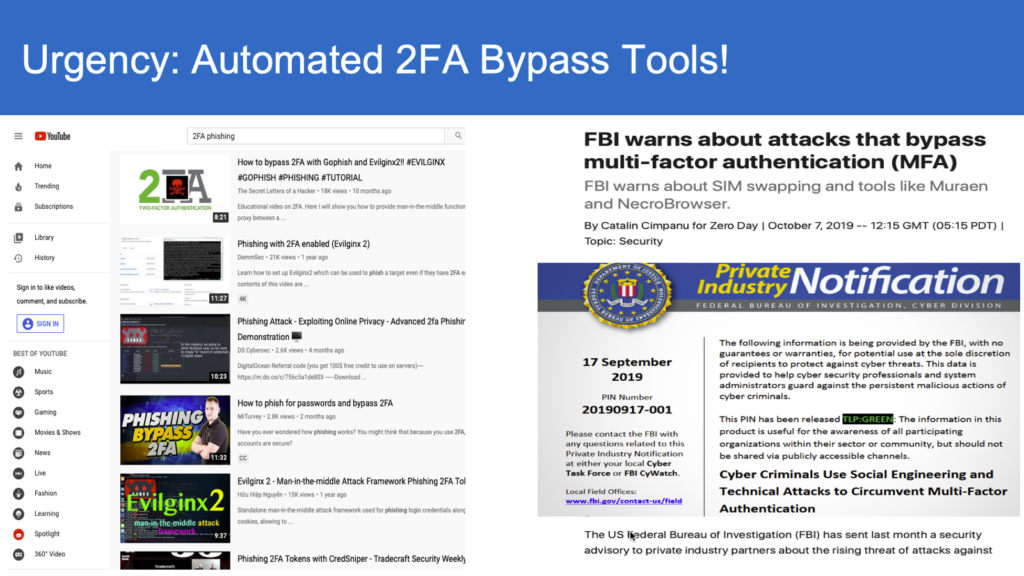
Since the release of Modlishka, by Poitr Duszinski, as a training tool on real-time proxy as a man-in-middle attack, cyber security world has been put on notice. Since then various enhancements were made by Evilngnx2 and Muraen etc.
The tool is now weaponized as published by a research team at Microsoft, that 10000 organization have been targeted by this “MFA bypass” attack. MFA bypass attack is not new, known to the cyber security community long back in early 90’s. Thanks to platforms like Github, exchange of large code base is now possible across open communities.

In simple terms, MFA Bypass means, the attacker will intercept the communication channel between a user and authentication system, and wait until the authentication completes successfully with usual password and “Other” multi-factors including – One time passcodes, SMS, out-of-band approvals in mobile app etc. and grab the authenticated session cookies. In this way, the attacker does not need to chase your passwords and other multi-factors authentication (MFA) in-use.
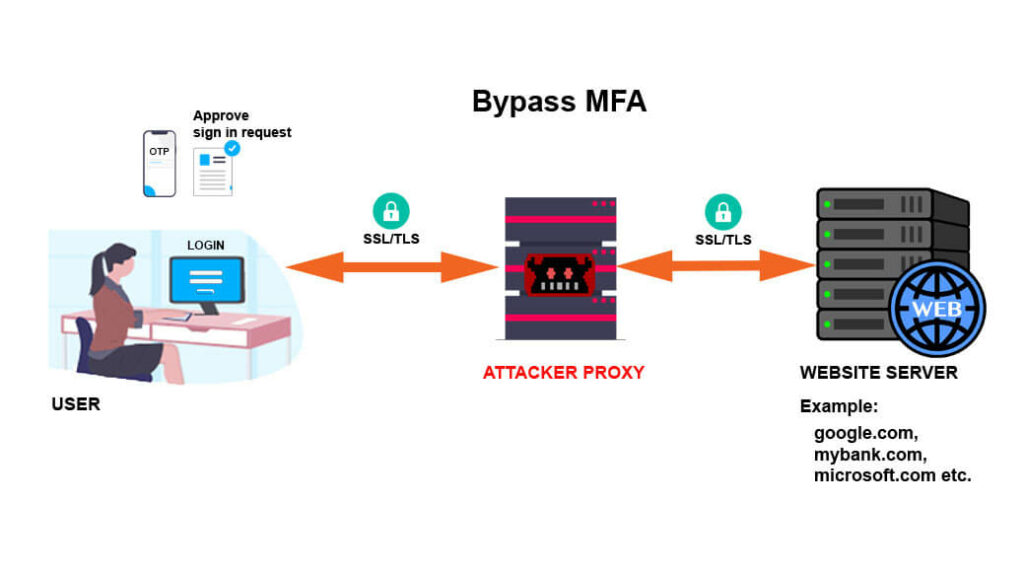
While the security community has been screaming – activate MFA ; but the hacker community has caught up with technology and now we need a way to secure critical online applications with better than “legacy” MFA schemes.
Here comes the new concept of bearer-aware authentication codes that are anti-[theft, replay, phish, bypass]. A novel patented authentication scheme that is pioneered by iLogSafe.
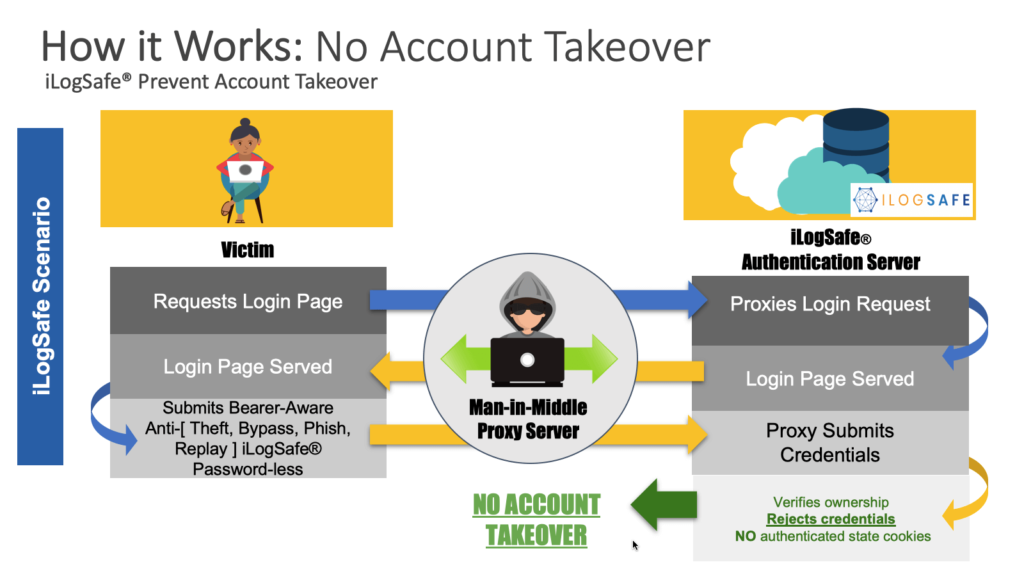
Sure, we are coining a new term, but the concept has been there since the introduction of travelers checks in good old days. Carrying cash while traveling would risk the cash stolen. Travelers checks were introduced such that even if they are stolen, they are useless for thieves with additional security verification.
In the same way, bearer-aware authentication codes are cross-checked against replay, spoofing in order to authenticate a user. These codes are useless for hackers and when a real-time proxy is looking for authentication cookies, they would be absent as authentication system detects spoofing and fails the authentication session.
Benefits of bearer-aware authentication are:
- No uprooting of the existing authentication – same flows work, but you get the security against MFA Bypass, man-in-middle, Keyloggers, etc.
- Passwords are optional, you can phase them out once you are comfortable with Bearer-aware authentication codes
- No worry of credential leaks – stolen bearer-aware authentication codes are useless for hackers
- Best of all, not tie-up of your site-urls with user accounts – imagine you are in an M&A, or you want to rebrand your site, you can avoid thousands of users re-registering with other authentication schemes
- Super easy, intuitive, scalable and portable
Watch our anti-[replay, bypass, phish] solution live here