Protect your cloud files, including Microsoft Office 365 and Google Apps
iLogSafe ’s unique inexpensive and scalable security approach provides:
- A fearless online banking/e-commerce environment by eliminating the threat of stolen passwords, providing a boost in customer confidence in your online transactions
- Robust security without the need for costly hardware (tokens, key fobs, etc), out-of-band channel SMS (short message service) messages on cell-phones, or the installation of high-maintenance end-user software while retaining the simple user interface and experience required by your online users
- Several orders of magnitude of increased security compared to the password and challenge questions, such as “What is your pet’s name?”
- Greatly reduced security costs by eliminating layers of ineffective security today, typically providing a full return on your investment (ROI) in one year or less.

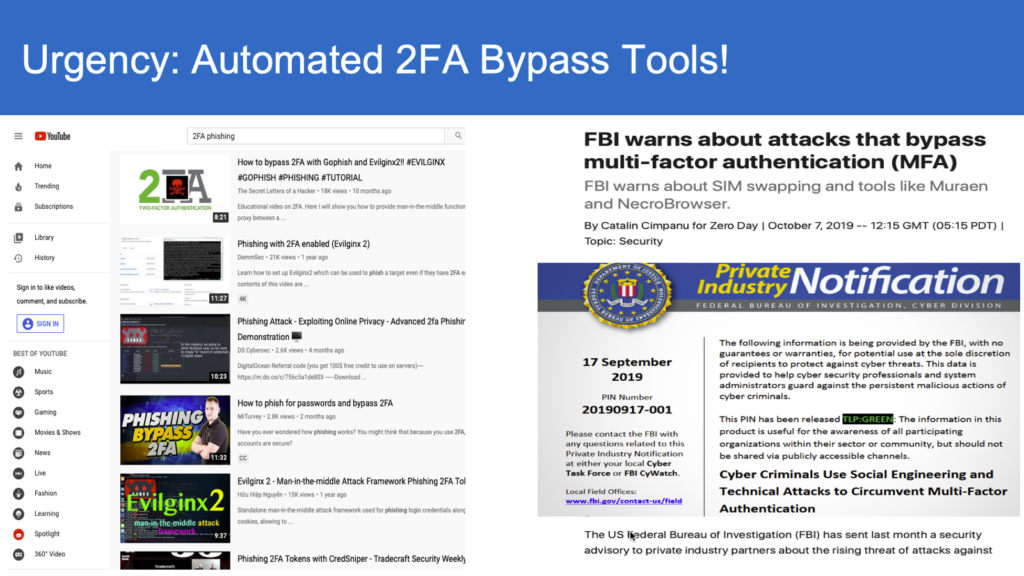
According to the Gartner Group, the number one threat to online banking and E-Commerce is the theft of security credentials like user login IDs and passwords. Fraudulent “phishing” is a serious threat to secure online transactions, luring even the most sophisticated users into parting with their security credentials. A recent Gartner survey stated that over 5 million U.S. consumers lost money to phishing in the twelve month period ending in September 2008. The figure represents a whopping 40% increase over the number of people victimized by phishing during 2007, per Gartner. Banks and other financial institutions have been the primary victims, having lost $3.2B in 2007 alone.
Phishing sophistication, through either social engineering or infection of end-user PCs, continues to increase in both magnitude and difficulty for timely detection, even for the sophisticated online users. To make matters worse, even if users do not provide any useful information when they land on “Phishy websites”, there is a likelihood that, by simply clicking the link they initiate the invisible background installation of key loggers, malware, or viruses.
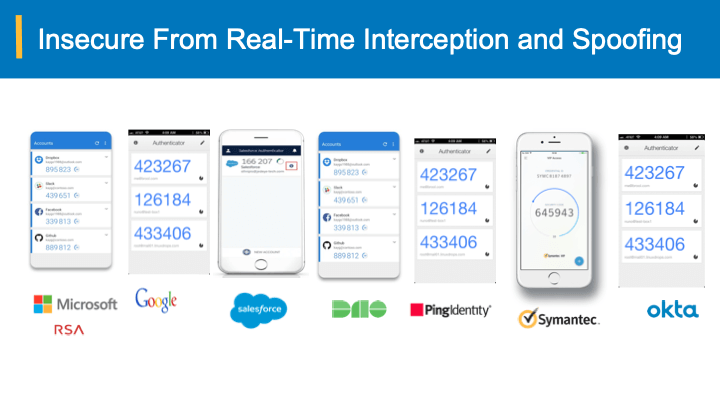
Many, institutions rely on a password and an associated challenge question for secure online access. No matter how high-strength a password is, online users are always susceptible to sophisticated phishing, key logging, and several other forms of attacks. Further, challenge questions, even though uniquely configured by each individual user, serve at most as weak secondary passwords, having the same vulnerabilities as their primary password. Even if pre-configured pictures and phrases are used to alert the online users, security may be readily compromised which is a well-known fact based on numerous hacking incidents that the industry witnessed.
security solutions
Strong authentication for all industries
Robust, easy-to-use digital security solutions for multi-industry