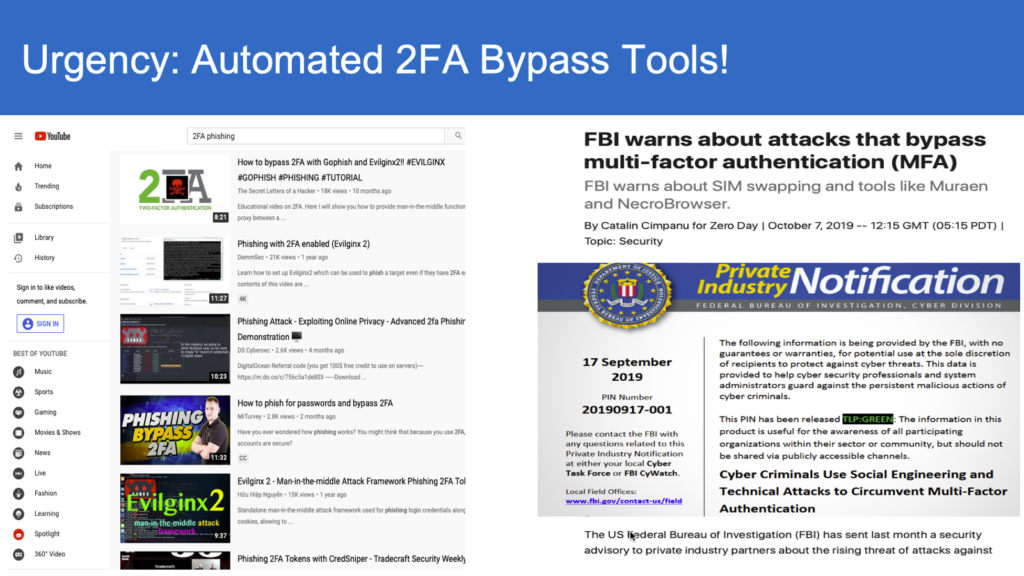
It’s true, two-factor authentication is no longer enough to protect and safe-guard against phishing attacks. As threats and attacks become more sophisticated and attackers adapt to the increased utilization of two-factor authentication (2FA), it’s evident that more is needed to thwart attacks and safeguard individual and business data.
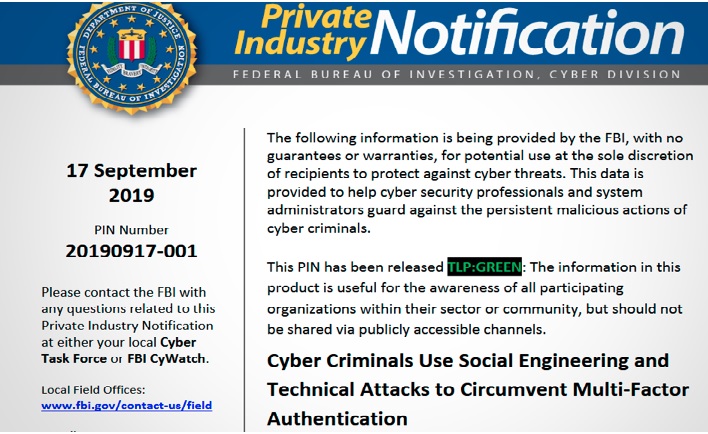
The limitations of 2FA have been outlined in a report released by the Federal Bureau of Investigation (FBI), wherein details of recent attacks reveal how hackers were able to bypass two-factor authentication protections and gain access to confidential data. This includes attackers utilizing a SIM-swap approach as a method of gaining access to personal banking information that was protected by a one-time mobile pass-code. This approach allowed the attacker to first gain access to and control of the victim’s phone number, and subsequently using that number to access banking data.
Moreover, the release of Muraen and NecroBrowser has proven that tools can be developed to not only bypass 2FA, but to do so with relative ease.
So, what does that mean for the continued use of two-factor authentication?
Two-factor authentication remains an important part of mitigating risk and protecting businesses and individuals from phishing attacks. Instead of abandoning 2FA, users need to take these risks seriously and take full advantage of security measures available in the marketplace.
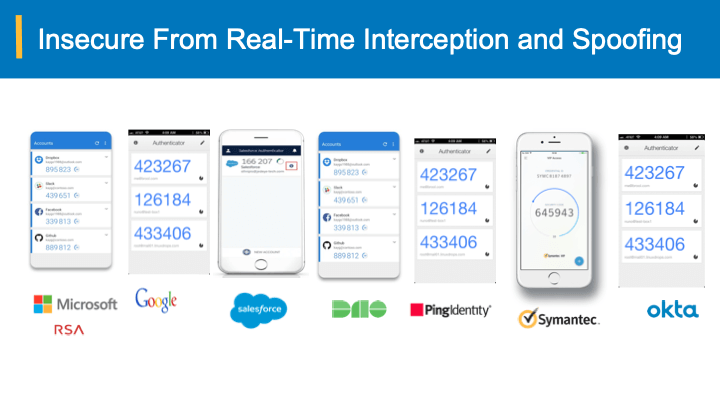
Businesses need to be proactive when it comes to security and implement measures to protect themselves. ZDNet recommends choosing a stronger 2FA mechanism that is not as open to “social engineering tricks.” Towards such measures, one can take advantage of the newest innovations in the “bearer-aware” OTP technology that can detect any intercepted and spoofed/proxied credentials to prevent account take overs that are the leading cause of 81% percent of data breaches and online fraud.
The Risk is Significant for Organizations of All Sizes.
It’s important to note that the risk of attacks exists for all individuals and all businesses regardless of size.
According to the Hiscox Cyber Readiness Report, nearly half (45%) of all business surveyed were victims of at least one cyber-attack in the past year. Key findings of the report show that attacks on small and mid-size businesses are on the rise, and even more troubling is that these small and mid-size businesses are generally less prepared to thwart attacks than larger corporations due to limited resources or lack of awareness of cyber risks, making them increasingly vulnerable to attackers.
So, what can businesses do to protect themselves?
- Educate yourself and people working with your business. Provide training on what cybersecurity is, how to identify risks or threats, and how to protect personal and business data.
- Invest in adequate protections, including anti-virus, 2FA, etc. to protect your business assets.
- Rely on trusted experts in the field to assist you in implementing the right tools and processes to protect your data from attackers.
Addressing MFA bypass
Two-factor authentication has limitations and vulnerabilities, it is not a perfect solution. Attacks are becoming more and more sophisticated in order to bypass the barriers 2FA has introduced. This means there’s risk to individuals and to business, small and large.
The good news is that there are steps you can take to address the limitations of 2FA. While layers of defense is a best practice, and are essential in the constantly evolving cyber-threatscape, there is a new bearer-sensitive authentication solution that detects any intercepted and spoofed credentials. This will practically eliminate all the credential phishing and multi-factor bypass without changing any of the current infrastructure.
For more details/demo and whitepaper, please fill-out our form here.