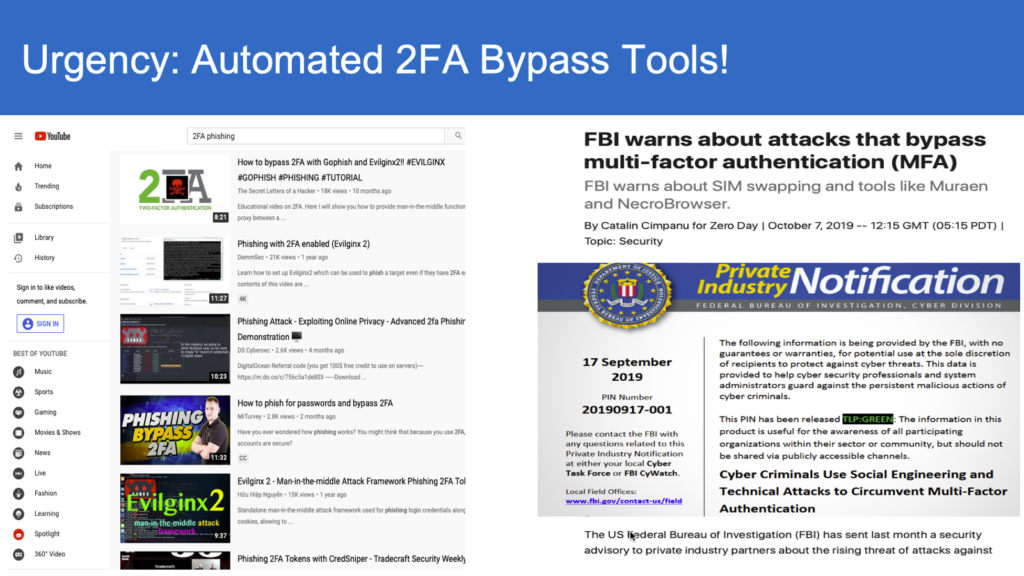
As per Verizon data breach report, 81% of data breaches and Financial fraud trace back to credential spoofing and account take-overs. With the advances in automation of Phishing and other social engineering hack-tools such as Modlishka and Evilngnx , the real-time proxying of the victim session with authentication eventually leading to session-hijack and account take-overs is prime for weaponization.


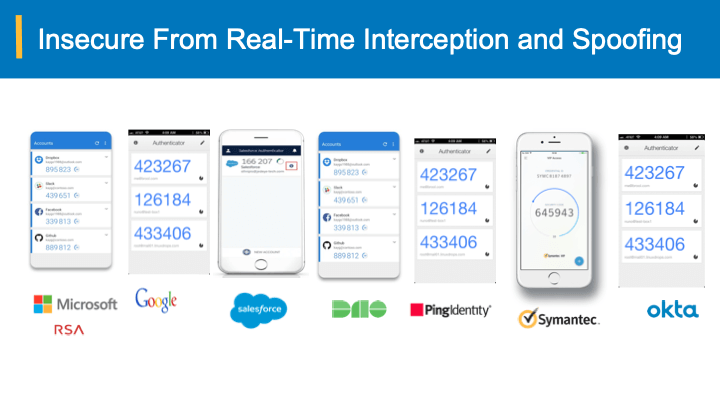
All are susceptible to spoofing
Let us step back and see the fundamental problem with the current popular MFA schemes.
A simple bearer instrument concept in Finance would serve well to illustrate the fundamental attribute of _all_ the current popular authentication schemes. In good olden days, we used to carry cash ($) currency and when the cash was stolen, the cash can be expended perfectly by the usurper. This is due to the fact that currency cash is a bearer instrument and holder of the instrument can expend it and needless to say that was the genesis of traveler’s checks.
Looking through the same lens, the passwords, one-time passcodes (hard tokens and software app-based), SMS schemes all suffer from the same — bearer-agnostic attribute. This is fundamental root-cause of all the attack vectors on credentials such as keylogger malware, phishing, main-in-middle (proxy) that can steal/intercept your credentials even time-bound (even momentarily).
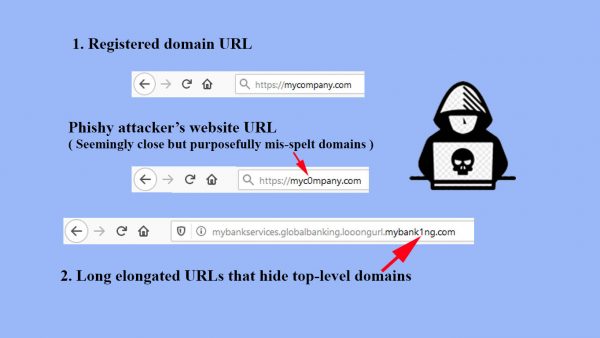
This is exactly why the problem man-in-middle snooping/intercepting on the credentials has been a challenge to the online authentication schemes. Several schemes that were proposed were made ineffective by the ever evolving and sophistication of the attacks. For example, the SSL padlock that appears when a ssl certificate matches with the domain can be easily forged by longer urls (e.g., services.mybank.services82981-xyysuooos-jasjllasl-global-some-more-chars-myphish.com) and with a matching ssl certificate of the top-level domain “myphish.com”. This is due to the fact that browsers can only visibly display limited portion of the long url and users just don’t have a chance to look at the complete url, while the browser also matches the top-level domain, and displaying a safe padlock misleading the users that they are on the legitimate site.
This vexing problem of credential-phishing and spoofing of credentials can be easily addressed with Anti-Phish Codes. Anti-Phish codes are specially generated codes that even if intercepted and spoofed for authentication, the authentication system can detect the submission of spoofed codes and thus the authentication attempt fails. As such, Anti-Phish codes prevent the session-hijacking as no authenticated state cookies or tokens generated by the authentication server and thus fraud resulting from account take-overs are eliminated.
As a patented technology that is the only solution without the need for additional hardware, dongles, the Anti-Phish codes can bring in much-needed unspoofable anti-phish codes for the enterprise security, safe guarding the data assets and eliminate financial fraud due to account takeovers.