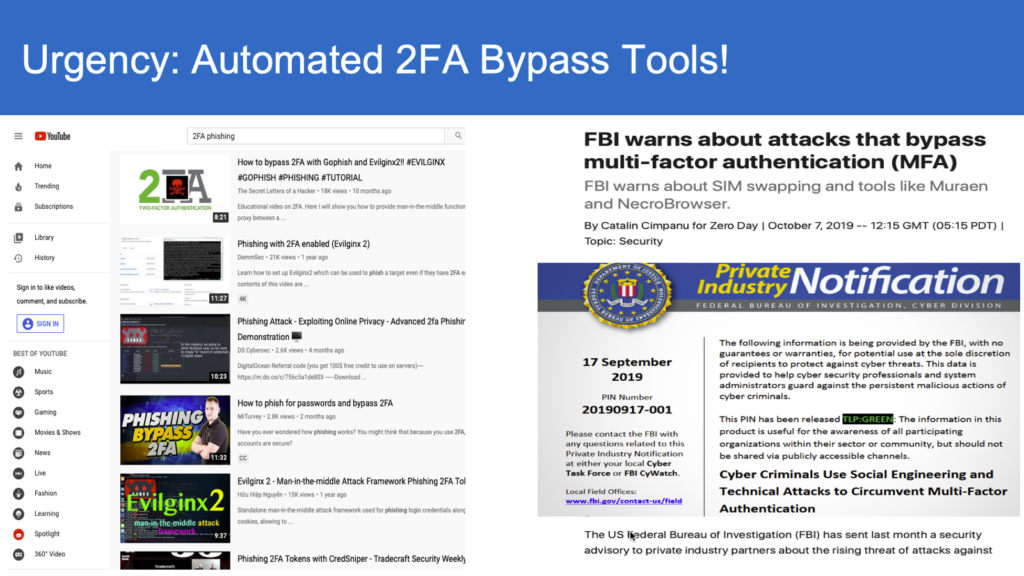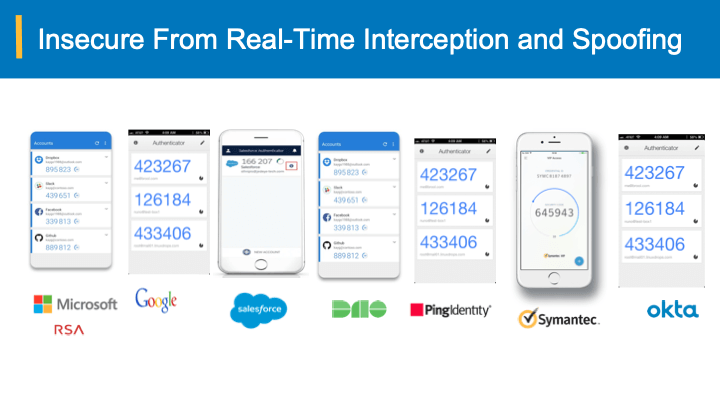
Seemingly look-alike URLs are the primary vehicle for Phishing, that results in potentially credential compromise and account take-overs. Such type of attacks have resulted in 81% of data breaches and online-fraud as noted by the Verizon’s data breach report.
As such technologies like FIDO have emerged, to combat Phishing URLs, through lock-in of URLs during the registration of a user account with public-private keys stored on the end users devices. The idea is to have the automatic checks against look-alike attacker’s phishing URLs and not rely on the human eye’s ability to distinguish Phishing URLs.
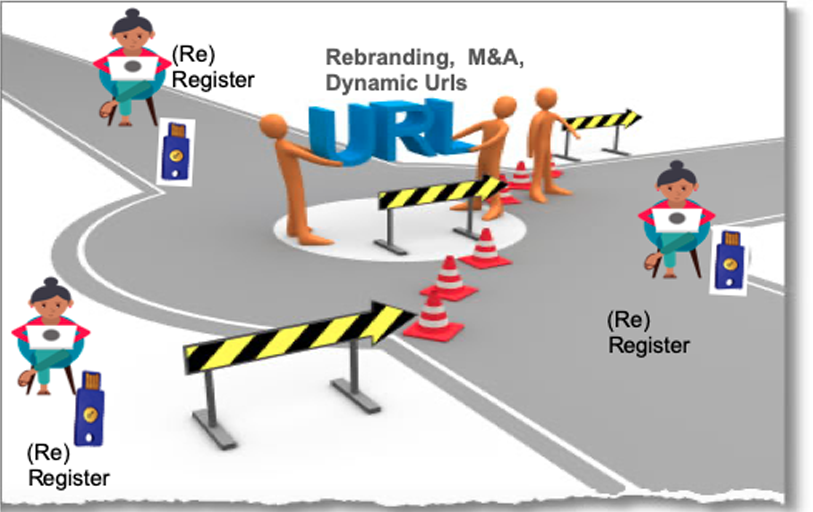
Several potential issues/constraints arise with the user authentication tied to the URLs at the registration. These can be summarized as follows
- URLs of the website cannot be changed (inflexibility) once the user registers’ their devices.
- In the case of a change in the url, all the users need to potentially re-register, and this applies to all levels from sub to top-level domains
- No dynamic urls can be used with such URL tie-in at the registration time
- When merger and acquisitions need rebranding and change in urls
- Long urls and several distinct websites, will constrain eventually the memory capacity of the devices
On the other hand, The Bearer-aware credential-based authentication does the job of securing against any spoofing and phishing (including real MiM proxy ) attacks with
- No tie-up to URLs during the account setup/registration
- No additional hardware required and cost-optimal
- No risk of relying on authentication agents at the user’s end
- No changes to applications and federation of identities
- Scalability across apps and users
As discussed in the Authentication tied to public keys at the relying party does not bring any additional risk reduction, when the relying party database is compromised compared to shared secrets.
A recent trend that industry has witnessed is that the SSL certificates match the top-level domain of the seemingly but intentionally mis-spelt and are leveraged to suppress any browser warnings on the SSL certificate mismatch.
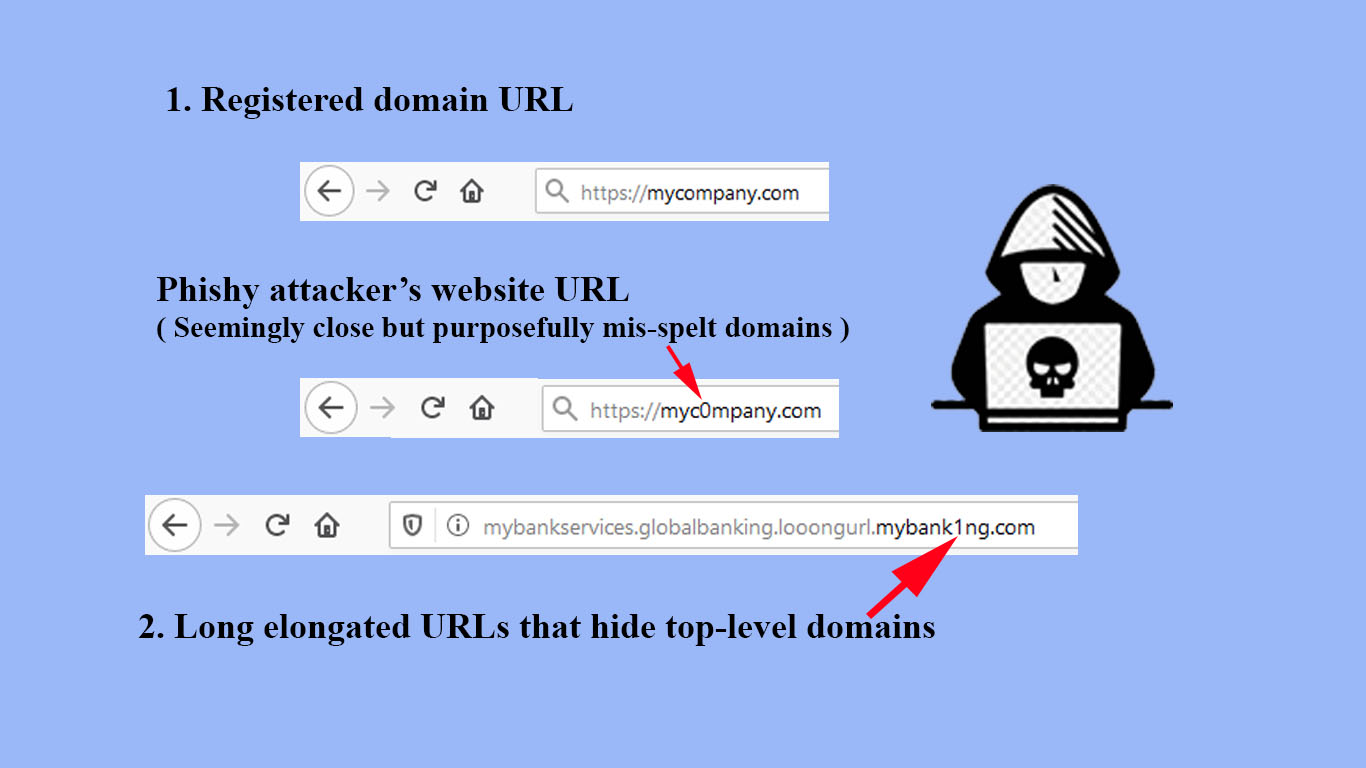
As such the users most likely are lured into parting away with their credentials and leading to account take overs.
The Bearer-aware credential-based authentication does the job of securing against any spoofing and phishing (including real MiM proxy ) attacks with no additional hardware expense and changing to applications and URLs all at a fractional cost with excellent ROI within a year.
For more info, please schedule a demo with us.