Every industry, even those with a limited online presence, are impacted by the interception and spoofing of stolen credentials, and most notably, there is a significant risk to organizations in the finance, healthcare, information services and government sectors.
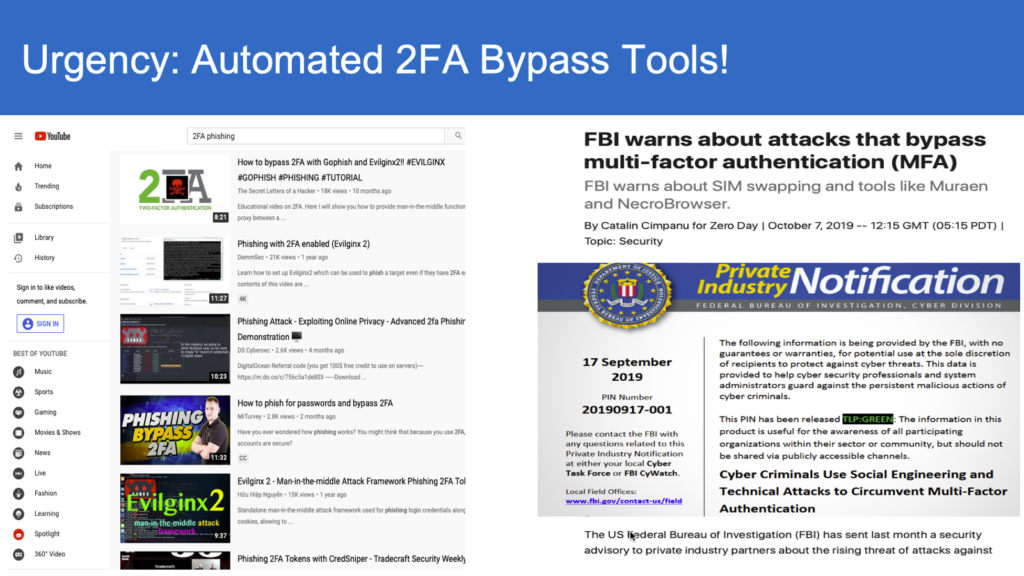
The attackers either create a phony login page or hijack an existing login page, and more recently with sophisticated automation in real-time proxying, acting as a middle man, attackers are able to intercept and steal user credentials or bypass multi-factor authentication user, eventually lead to fraud and data breach across the enterprises.
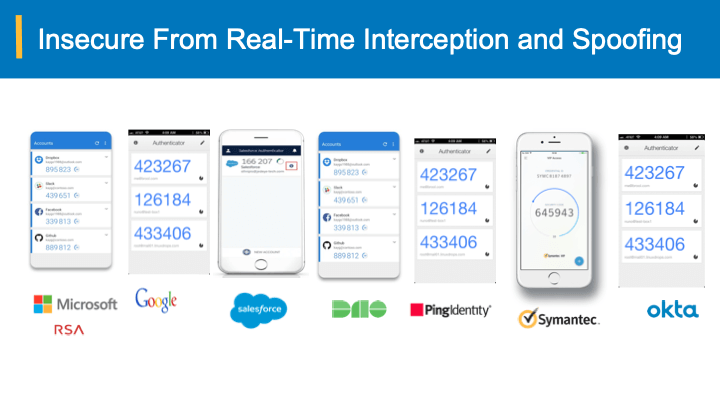
The attacks on credential stealing and spoofing are successful due to the bearer-agnostic nature of passwords, one-time passcodes etc. Whoever holds the stolen credentials can impersonate to the authentication system and take over the accounts (for more details on this, see our article “Why your password+SMS+OTP MFA fall short”).
It’s a real risk. Credential compromise accounts for 81% of data breaches in the past years, and in 2018 alone the financial fraud amounted to $12B with three times increase in account take overs.
In part, this issue stems from lack of training and awareness. A recent study showed that 81% of the data breaches in the past years were a result of credential compromise. In Proofpoint’s State of the Phish 2019 Report, users across the globe were asked, “what is phishing?” Of all respondents, 17% of them answered incorrectly and an additional 17% accepted that they did not know.
However, training and user awareness is not the only missing piece to the puzzle to prevent phishing attacks.
Why isn’t training enough?
When we talk about training and awareness to thwart attacks and threats, we’re talking about being able to identify inaccurate URLs and domain names, key identifiers in fake emails (i.e. consistent grammar and spelling errors), and disingenuous attempts to solicit funds or personal identifying information. However, studies have shown that training and awareness in these areas is not enough to stop individuals (including your employees!) from succumbing to phishing attacks.
The sophistication of email attacks broadens the risk to individuals and business. Fraudulent emails are made to appear as if they come from verified sources, whether that is a business or another individual. These types of emails make up 90% of all email attacks And with 86% of these cases being impersonation of a business, there is a significant risk. There are technologies that can thwart these attacks; however, they often are not implement appropriately, leaving businesses open for attacks.
Additionally, even when individuals are aware of the potential risks associated with emails links and, research suggests that curiosity may compel an individual to click on links from unknown sources. In an experiment conducted at Friedrich-Alexander-Universitat, 20% of recipients clicked on the link in an email from an unknown sender. Moreover, when emails used basic personal information, such as an individual’s name, the likeliness to click the link increased to 56%.
Information overload is another factor contributing to issues surrounding account takeovers. The National Institute of Standards and Technology proposes that individuals can easily become overwhelmed with the ever-increasing areas of risk associated with technology. For some, this leads to and individuals begin to overlook potential threats and succumb to the attacks against them.
Wait, what about my SSL padlock? 
Padlocks in the SSL/TLS communication have been introduced to ensure users have a visual clue to the end-users with further browser warnings and alerts on potentially harmful websites and ssl communication channel. However, with the misleading elongated urls and the tail-end top-level domain matching with the ssl certificate presented, the attackers are able to play the middle-man, intercepting the victim’s traffic across the Internet (for more information, please take a look at “Anatomy of Multi-factor authentication bypass” ).
Final layer of defense with unspoofable authentication
While layers of defense is a best practice, and are essential in the constantly evolving cyber-threatscape, there is a new bearer-sensitive authentication solution that detects any intercepted and spoofed credentials. This will practically eliminate all the credential phishing and multi-factor authentication bypass without changing any of the current single sign on (SSL) infrastructure.
For more details/demo and whitepaper, please fill-out our form here.