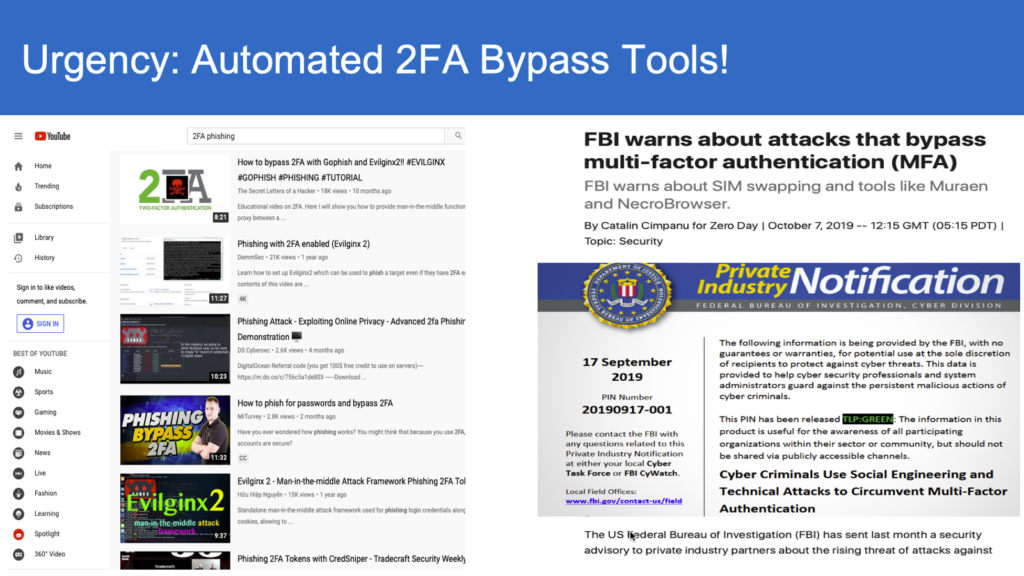
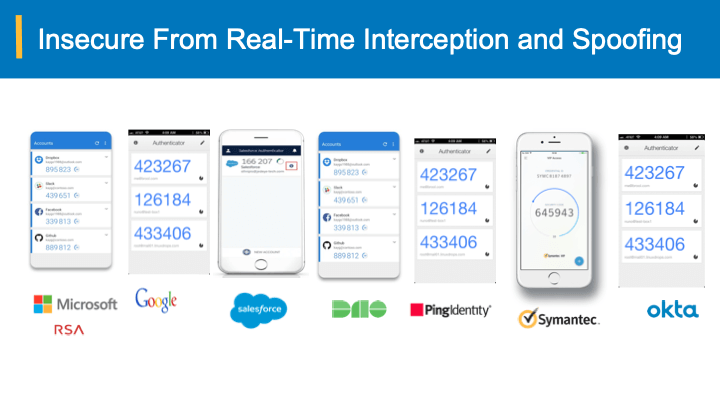
The level of sophistication that exists with automation and real time proxying of 2-FA phishing puts all users at risk, potentially leading to devastating data breaches and financial fraud transactions. Without investment in equally sophisticated technology to thwart attacks, the responsibility lies completely on the individual user to identify and stop attacks. However, with the recent spate of developments, including Modlishka, Muarena/NecroChrome, on automation and real time proxying user training on phishing is only partially effective at best, leaving organizations (and users!) exposed and vulnerable.
Where’s the Risk?
Serious risk lies within real time relays and elongated URLs with top level domain SSL certificate matching.
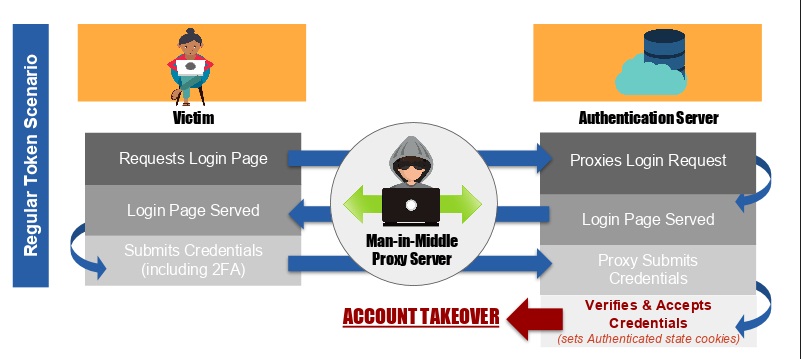
To start, the real time relay of authentic sites, such as a bank or other institution that has data or financial assets to protect, ensures that the fraudulent website served to the victim appears genuine, hosting the same content as the authentic site.
Additionally, long urls with top-level domain SSL certificate matching have also made secure-locks on the browser unreliable indicators on the legitimacy of the pages being served to the victim. These elongated URLs hide the real phishing top-level domain, and with the legitimate SSL certificate makes it impossible for the browsers to rely on SSL certificate match with the phishing URLs.
Here’s a look at how these attacks work.
When you look at the URL below, it will be hard to see the top-level primary domain “phish.com” due to the partial display of the url that’s visible in the browser.
HTTPS://LOGIN.MYBANK.SERVICEGLOBAL.USA.JKLDCASLKJHDASWQOIWQOHJKSDGHDSH.PHISH.COM
The user might pay attention to only login.mybank and for the lock symbol on the ssl certificate match in the browser. As such the user never gets any browser warning. The victim is tricked into believing the page is the authentic web site and proceeds to enter their credentials including 2FA.
As the credentials are bearer-agnostic, they can be perfectly spoofed by the attacker’s proxy server and relay the credentials for login. Upon verification of the submitted credentials that belong to the victim, the authentication system transitions the session state to an authenticated state with the help of session and cookie variables to mark it as authenticated session. At this point, the attacker proxy has all the data for accomplishing an account takeover of the victim.
Recognizing the Impact on Users & Organizations
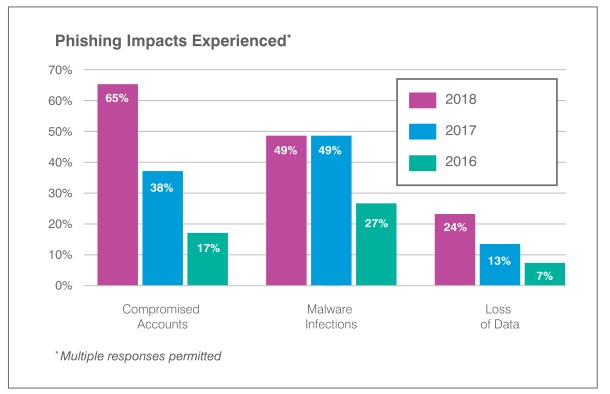
According to survey results released in ProofPoint State of the Phish 2019 Report, organizations disclosed account comprise as the most commonly experienced phishing attack (65%). Furthermore, the report notes that there has been a significant increase in the experience of loss of data (+17%) and malware infections (+22%) from 2016 to 2018.
The threat is substantial and growing when it comes to automation and real time proxying of 2-FA phishing. The question isn’t “if” the phishing kits will be weaponized but “when”, and with the threat they pose for users and organizations, what can be done about them? Read our article on what you need to do to address this 2FA credential phishing that can potentially lead to devastating data breaches or financial fraud transactions here.
These figures point to organizational awareness of phishing, but also indicates the need for more reliable safeguards. Recent trends on Phishing are extensively documented here. Additionally, phishing attacks on smartphones in particular is increasing by 85% year-after-year, which subsequently increases the vulnerabilities to organizations.