Many have been lost in the multi-factor authentication lingo. Yes, it is simple to explain about a) what you know, b) what you have , c) what you are, and finally d) what you do; all processes assumed to be repeatable and inimitable.
First, when we move beyond the first factor, the end-user is now forced to carry or behave in certain way that does not trigger a false alarm with the authentication system leading to a certain degree of inconvenience.
Second, when it comes to online user authentication, there is indeed no physical verification of the type and origination of the response. The fundamental mode of operation is that all the extra factors (other than the 1st factor) are translated and transformed into a response that is echoed back to and verified at online authentication system. Thus, it is the end response that finally counts towards authentication and not how it is achieved.
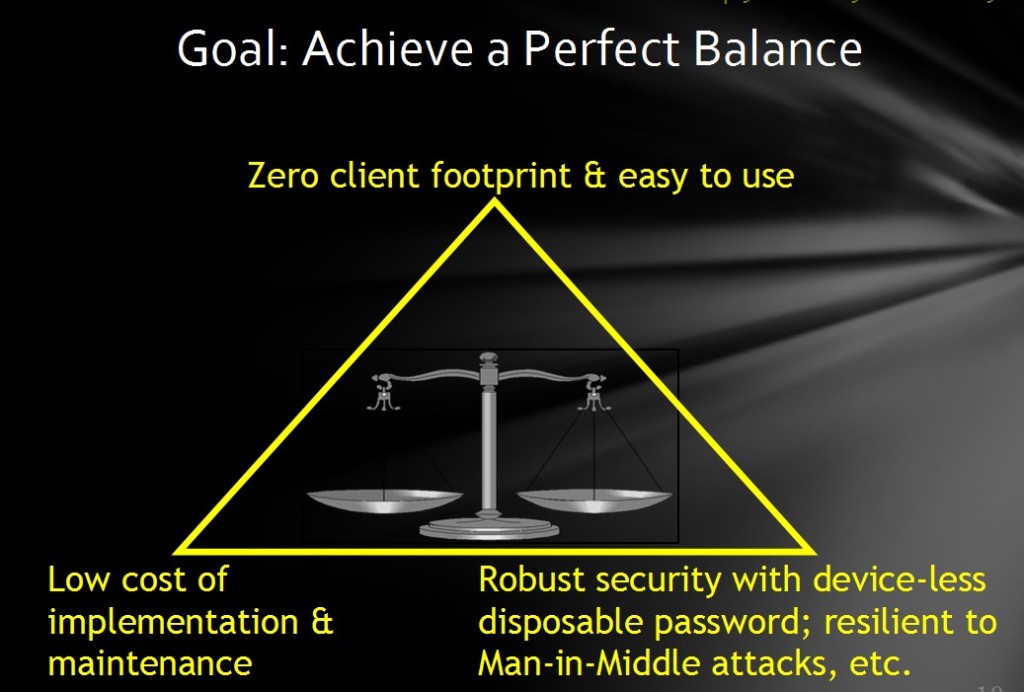
Let us examine the goals and desirable characteristics of any online authentication system (solution). They can summarized as follows:
- A tightly-coupled mutual assurance between the authentication server and the end-user
- Shared secrets should be individual (user-centric) and sharing of such secrets among the end-users should be reasonably difficult
- Response from the end-user should be ever-changing (dynamic) and ties it to the end-user
- Ability to authorize/authenticate on a transaction (or access of resource) basis
- Ease-of-use by the end-user and Ease-of-deployment (& maintenance) for the administrators
The first three in the above list ensure that the solution is resilient to Phishing and other password-stealing mechanisms. The latter two ensure that the solution is easy to implement, adopted by the end-users and real security is provided at a granular level balancing the convenience, while hackers won’t be able to piggy-back on their authenticated sessions.
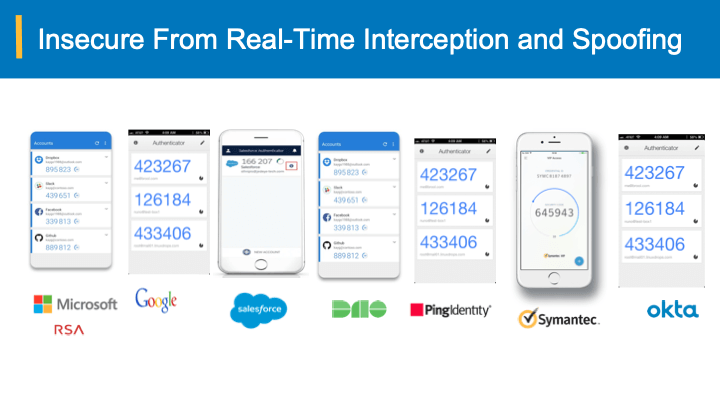
Solutions that bring in the dynamicity in the end-user response with the help of mapping (transformational) virtual keyboards (& grids) using the underlying passwords are still susceptible to Phishing. The universality of such mapping mechanisms (keyboards/grids) make them vulnerable to Phishing through duplication of such mechanisms to deduce the underlying passwords. These do not meet some of the items (requirements) in the above list.
Finally, when it comes to out-of-band mechanisms such as phone factors where the access codes are delivered via SMS text messages, there are two compelling reasons to have a zero-footprint (client-side) authentication, viz.,
- Online banking and other secure applications are increasingly being accessed and done through smart-phones. This would make cell-phones the main target of hacking for cyber thieves. As such one would need an extra out-of-band channel such as another cell-phone, to deliver access codes.
- Time-sensitive applications would totally depend on service provider network’s ability to deliver the access codes in real-time.
Therefore, it would be more convenient and desirable to have a strong zero-footprint authentication meeting the specified requirements such that the authentication is device-agnostic. Not to mention the hassles of carrying usb-tokens/keyfobs and their maintenance costs.
Summary: A strong zero-footprint (client-side) solution that can meet all the above criteria and achieve a good balance of ease and convenience is highly desirable. Yes, it challenges the traditional thinking (at least in practice) zero-footprint solutions alone cannot deliver the desired online/remote end-user authentication.