The latest cyberattack on SolarWinds showed that hackers are not only able to bypass highly secured identity solutions and gain access to multiple cloud environments, but they can also establish privileged access to systems and go undetected for months. By gaining control over compromised credentials and impersonating legitimate users, bad actors are able to move laterally and access virtually any program, application, or account.
SolarWinds is a company that develops network management systems for a wide array of customers. The recent attack included 425 of the US Fortune 500, various branches of the US Government, the Pentagon, the State Department, and hundreds of educational institutions worldwide. By surpassing multi-factor identity authentication systems (MFA) and impersonating users, the attackers successfully injected digitally signed trojanized components to control not only local company assets but also third-party servers associated with them.
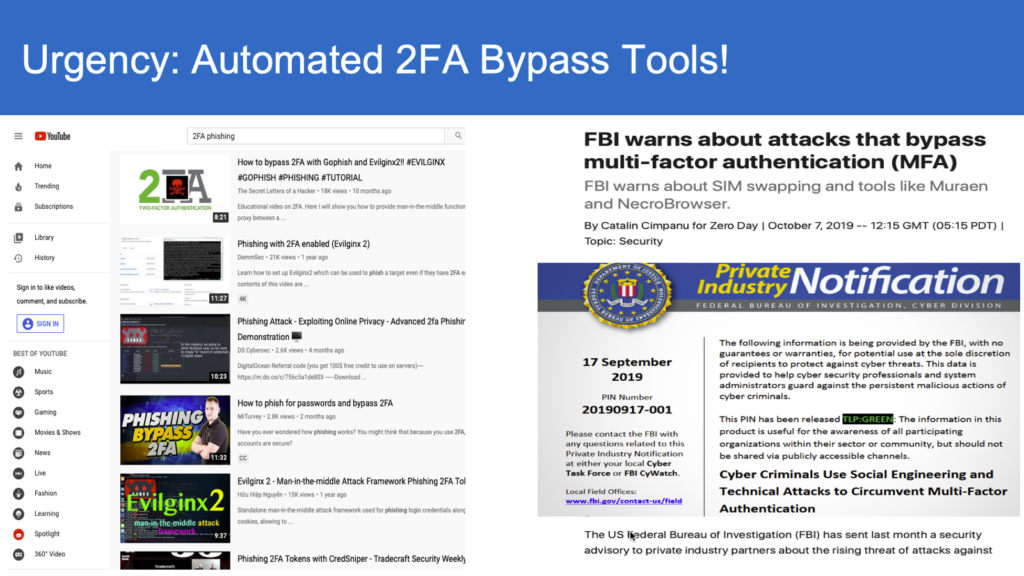
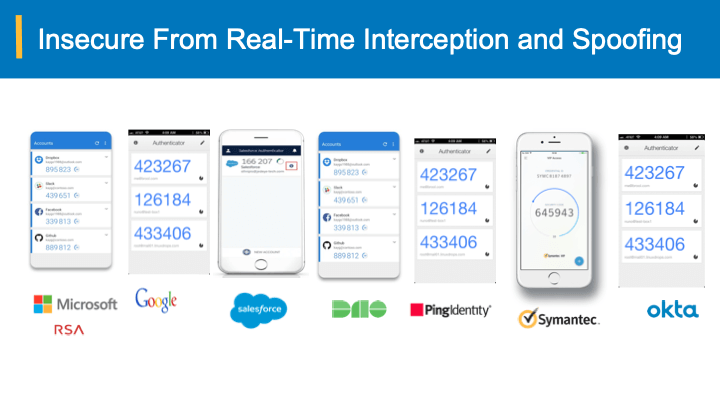
Since this unprecedented attack exposed over 18,000 SolarWinds clients, the cost of recovery is estimated to be over $100 billion. The matter gets even more complicated. Since the attack went undetected for many months, it created additional opportunities for future vulnerabilities and hacks that are hard to detect and predict now. While the CISA is still investigating the full scope of the breach, one thing is clear: MFA does not guarantee robust security and can easily be bypassed.

- MFA does NOT stop Business Email Compromises (BEC)
- MFA does NOT stop account takeover or social engineering
- MFA does NOT provide protection outside authentication
- MFA does NOT stop unpached software vulnerabilities
If Legacy MFA is not the ultimate defense solution, then what is?
We suggest exploring anti-theft, anti-spoof bearer-aware anti-theft solutions such as anti-phish codes. This latest cybersecurity innovation easily detects interception attempts and enables passwordless access to multiple applications. Without making any changes to your processes and systems, anti-theft codes eliminate the risk of credential compromise that lead to security breaches. They are quantum-safe and customizable for convenience and mobility.
While MFA depends on OTP and out-of-band approvals from the user who can be easily impersonated by advanced hacking techniques, anti-theft and anti-spoof bearer-aware credentials eliminate possible leaks and help fortify your incident management. They allow you to gain the ultimate control of authentication verification and eliminate the cost of added end-user authentication agents and certification. Schedule a demo to learn more.