The US hospital system has recently experienced an organized ransomware attack which was most likely linked to an ongoing series of targeted cyberattacks that affected numerous medical facilities.
Ransomware attacks are especially dangerous for healthcare because they pose a deadly risk to patients whose lives depend on the accessibility and accuracy of medical records. By injecting malicious software and encrypting hospital files, an attacker is able to block the victim’s access to the data and demand a ransom to restore it.
After the payment is received, the user is given instructions on how to get the decryption key and regain access to blocked files. The cost can add up to thousands of dollars usually payable in bitcoins.
As COVID-19 sweeps American hospitals, ransomware attacks in healthcare have also surged. Major hospitals in New York, California and Oregon fell victim to ransomware in 2020 alone. Some of them were even forced to operate on paper as their infrastructures went offline.
Increased cybersecurity risk is expected to worsen in the upcoming months. On October 28th, The FBI and the Department of Health and Human Services issued a joint statement about “imminent” ransomware threat to hospitals and the need to ramp up efforts to prevent future attacks. According to cybersecurity firm Check Point, the number of ransomware attacks in American hospitals has increased 71% in just one month, from September to October, 2020.

With ransomware on the rise, what can healthcare institutions do to protect themselves from the imminent threat?
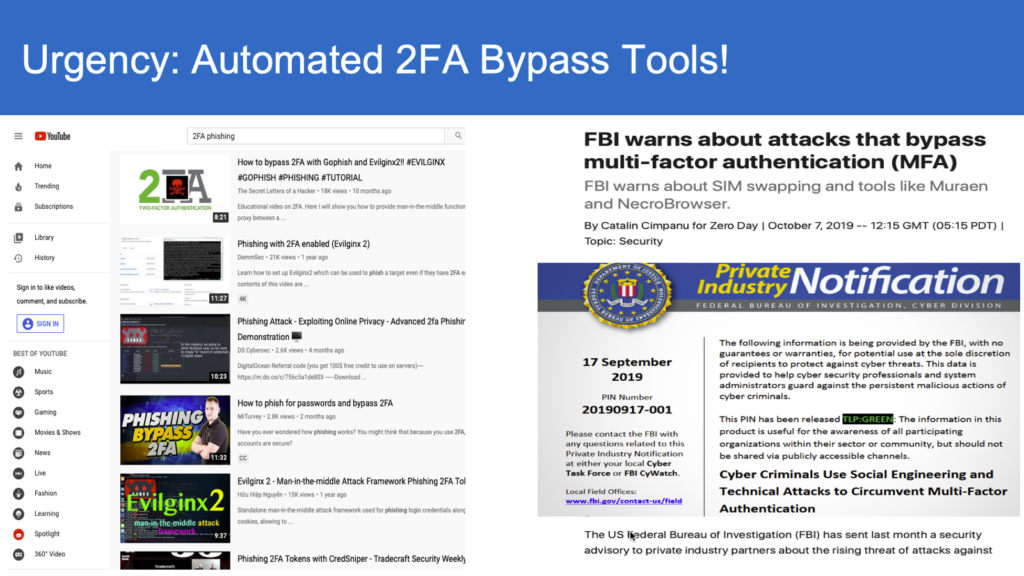
Sure, the US government can invest into more aggressive anti-hacking operations against dark web gangs, but it all starts with securing your authentication process. And the first step to ensure your login information never gets intercepted is implementing bearer-aware credentials.
Bearer-aware credentials is a part of a simplified authentication model that assigns a unique one-time passcode to a user and utilizes a server-generated watermark that can never be replicated by an intruder. You can rest assured that your login information is safe and can’t be intercepted or manipulated in any other way.
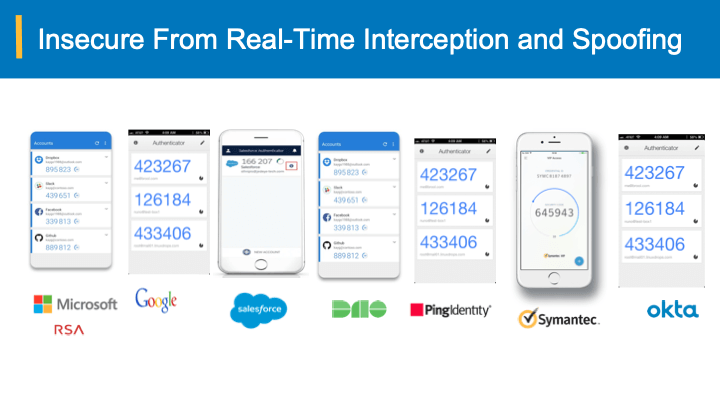
In contrast to bearer instruments such as OTPs, SMS and out-of-band authentication approvals, bearer-aware credentials act as a unique id card that, even if stolen, is useless to the offender. Bearer-aware credentials are completely secure even when your OTP gets spoofed. They are also immune to credential leaks and SIM card swapping.

If you are looking to eliminate the risks associated with unwanted credential sharing without making any significant changes to your applications and infrastructure while staying HIPAA – compliant, bearer-aware credentials is your ultimate solution. They will help strengthen your HIPAA compliance as means to mitigate and remediate identified cybersecurity risks.
Schedule a demo to see for yourself how easy it is to implement and manage bearer-aware authentication in your organization.