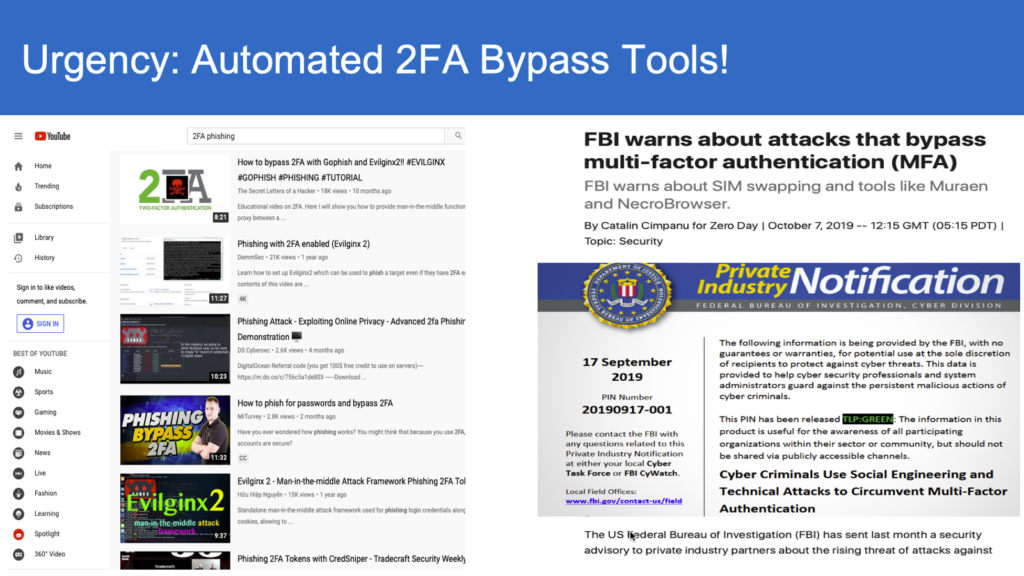
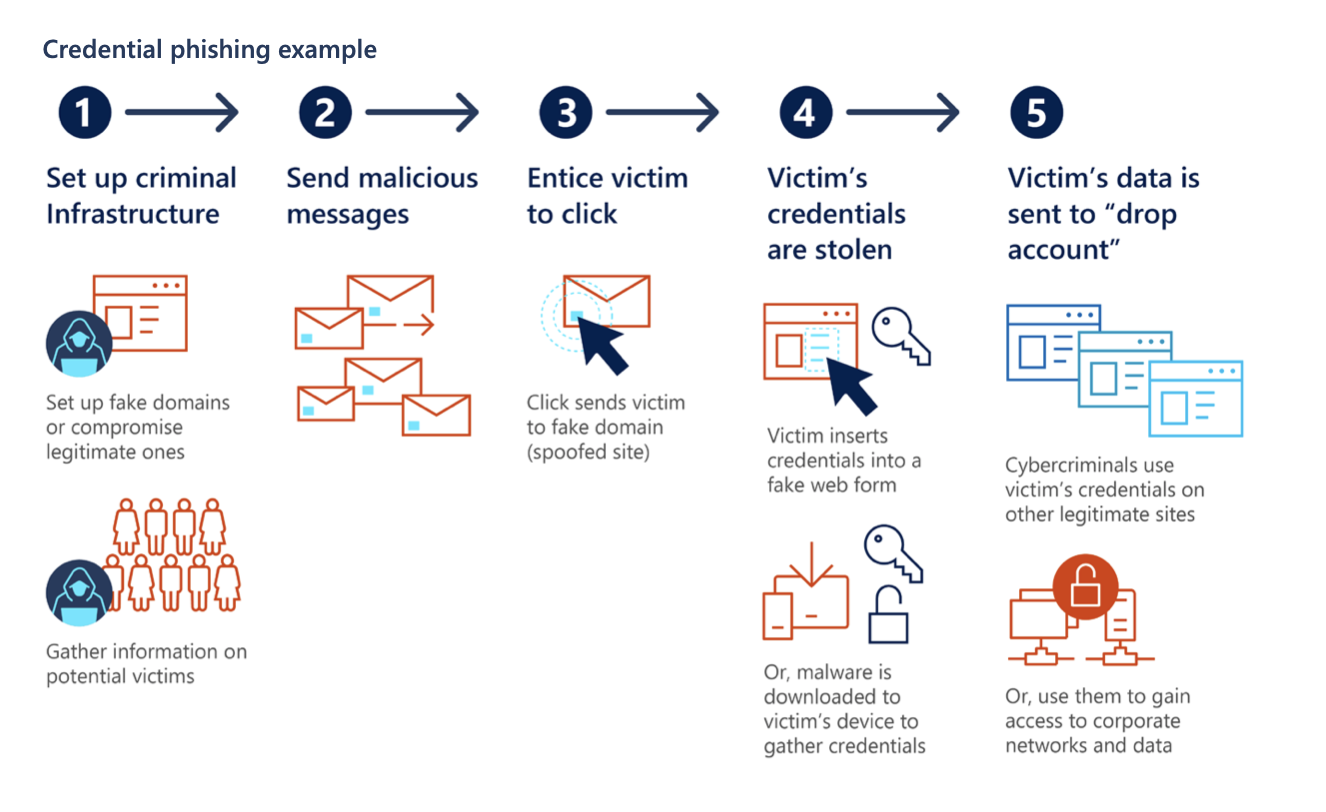
Microsoft has recently released its annual Digital Defense Report showing cybersecurity trends from 2019. This report illustrates that over time, cyberattacks and threats have considerably evolved into sophisticated technologies that are hard to forecast and detect even by the savviest of IT professionals. Credential phishing attacks are no exception. Cybercriminals became so elaborate, they are now able to hide malicious links in the email templates used by well-established enterprise-level SaaS services. They collect the victim’s credentials and gain access to legitimate systems within the targeted network.
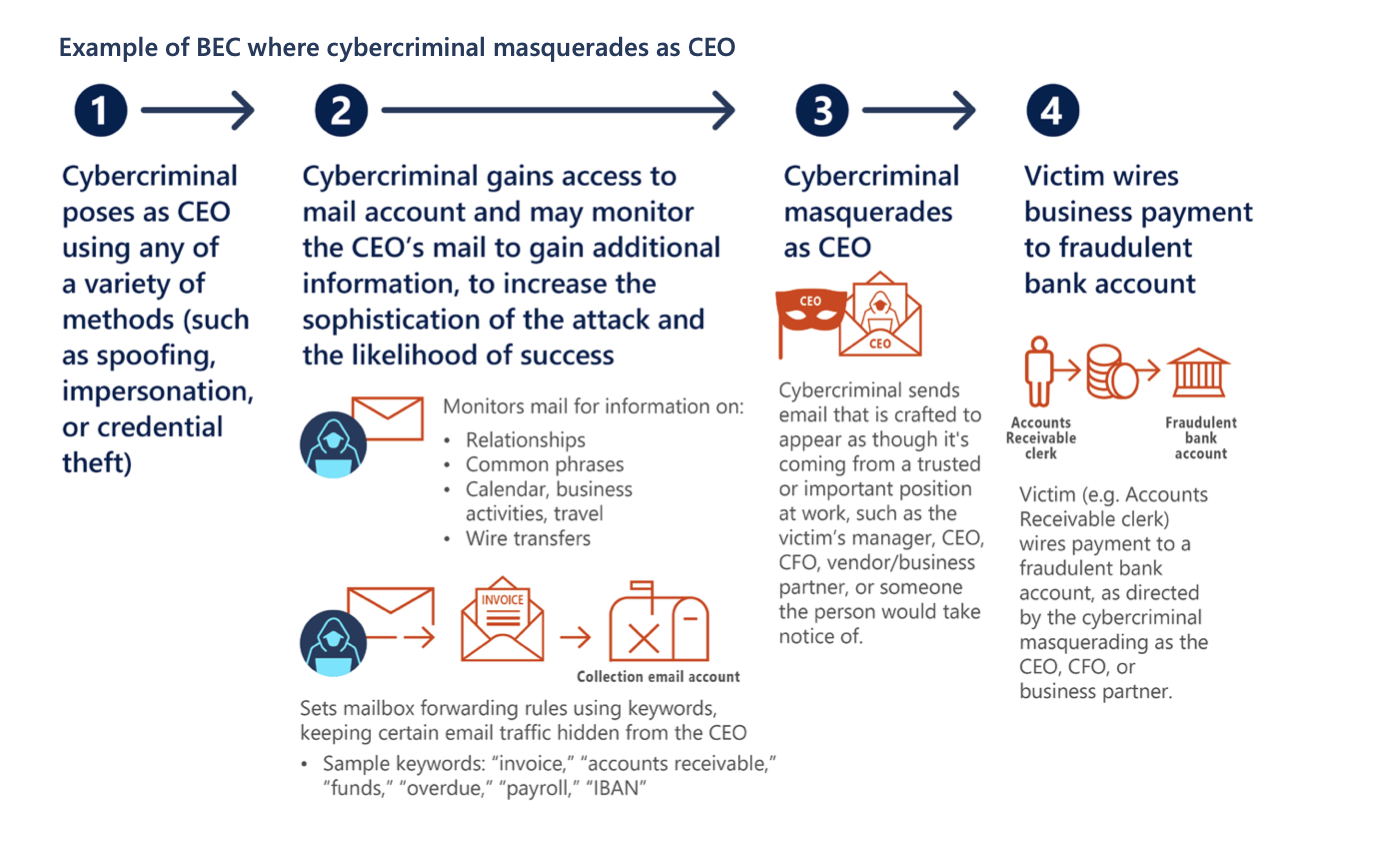
In addition to the advancements in credential phishing, bad actors are now able to apply business email compromise (or CEO fraud compromise) techniques to pose as a company C-level executive to steal user credentials or fraudulently request payments. At its core, this is a social engineering scam executed so flawlessly that it can victimize even the savviest professional.
The report also shows that overall, we are seeing a notable shift forward credential harvesting and ransomware mixed with the use of Internet of Things (IoT) devices. Microsoft presents significant research and data illustrating the magnitude of the latest trends:
- 13 billion suspicious and malicious emails with over 1 billion fraudulent urls were blocked
- Ransomware was the most common reason for incident response engagement
- Credential harvesting, malware and VPN exploits were common attack techniques
- 35% increase in IoT attack volume in the first half of 2020 compared to the second half of 2019
If the above numbers are at all convincing, it is now more than ever important to take steps in protecting your organization from malicious threats. No matter the industry, investing in the programs and people that can stop these trends from skyrocketing should be a top priority for every organization.
And it all starts with secure authentication…
The authentication process doesn’t have to be complex. Using bearer-aware credentials that prevent mission-critical logins from changing ownership is just as simple as obtaining a traveler’s check that can’t change hands easily. When your cash gets stolen, it can be used anywhere. Traveler’s checks are meaningless to criminals as they can only be used by a person to whom they are assigned to.

Bearer-aware credentials work similarly to traveler’s checks. They use an authentication algorithm that traces your information back to its original user preventing bad actors from reusing your unique one-time code. The algorithm uses the device’s digital watermark that’s generated by the server in response to a login request and can never be reused by an intruder.
This simplified authentication model doesn’t change your applications or infrastructure. It is entirely safe and unique only to your organization. If you wish to eliminate a chance for a direct interception that results in a credential theft, bearer-aware credentials are right for you.
Here at iLogSafe, we are committed to providing a unique bearer-aware anti-spoofing solution customized to your specific needs. With iLogSafe you can detect interception and shut down fraudulent sites before they even have a chance to attack. You won’t need to rely on creating strong passwords and storing them in your system which considerably simplifies your password management efforts. With our bearer-aware credentials, you can rest assured your SIM card is protected from swapping and transactional authentication stays intact.
Ready to learn more about the benefits of bearer-aware credentials and ways in which iLogSafe can offer system protection and peace of mind to your System Administrators? Let’s chat!