You do not carry large amounts of cash during your travel for the risk of the cash being stolen and thus carry other forms of equivalent financial instruments (such as travelers’ checks or that requires additional verification). This is because of bearer-agnostic nature of the cash that when stolen can be used by thieves.
Similarly, moving away from bearer-instruments such as passwords, Oath OTPs, Out-of-band approvals to authenticate the online users, bearer-aware credentials tie the credentials back to the user (similar to an agency issued verification card) and thus even when intercepted, stolen and spoofed they are useless for attackers to compromise the user accounts. On the Cyber security threat-scape, the fundamental issue that is exploited several ways by the attackers is the core nature of the spoofable online credentials – passwords, OTPs, SMS approvals etc. that are widely deployed.
Why bearer-aware credentials?
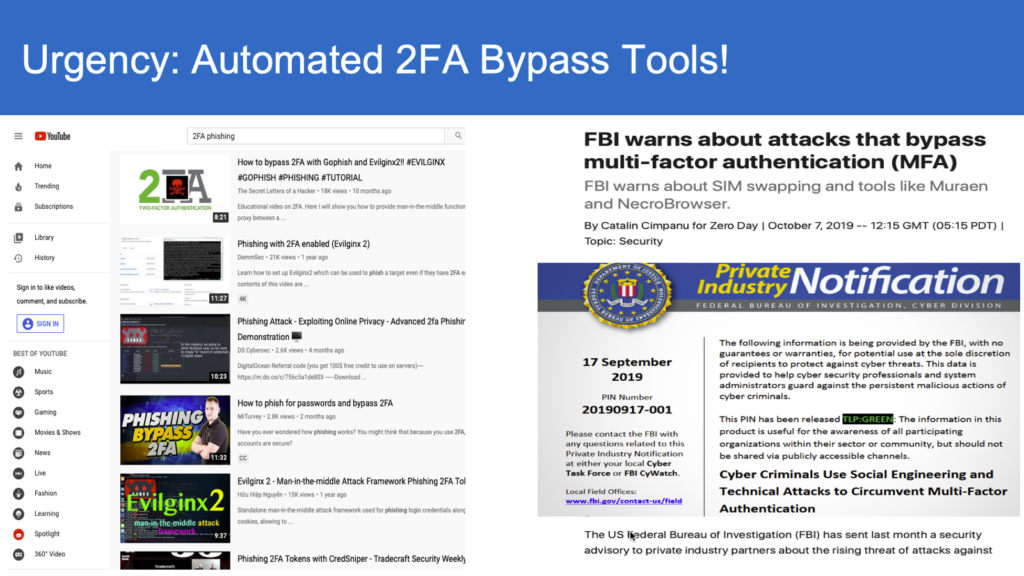
Looking closer at the such credentials, the core attribute is the bearer-agnostic attribute. In simple terms, if someone has your password, they can impersonate and login as “you” in the online Cyberworld. Same is the case with Two-Factor authentication schemes that deploy either OTP or out-of-band channel approval by the users. In fact several 2FA by-pass automation tools have surfaced in the recent past, notably Modlishka, Evilnginx and Muaren.
A Bearer-aware credential by definition uses some attributes of the end-user’s environment and ensures the submitted credentials are tied back to the user. As such, any attacker, when intercepts and spoofs the credentials with this bearer-aware property, would not be able to authenticate and take-over the user’s account.
What problems do they solve?
For starters, under certain good security hygiene environment, pictures are worth thousand words, the following can be addressed by the bearer-aware credential technologies:

Bearer-aware credentials can eliminate impact of leaks totally
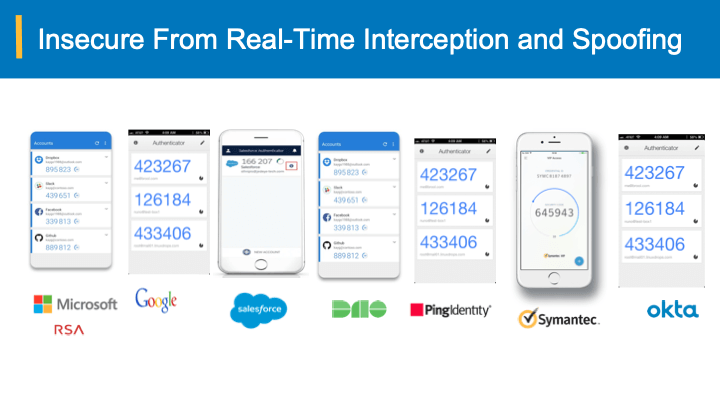
Bearer-aware credentials secure even when OTP is stolen and spoofed

Generating Bearer-aware credentials is immune to SIM
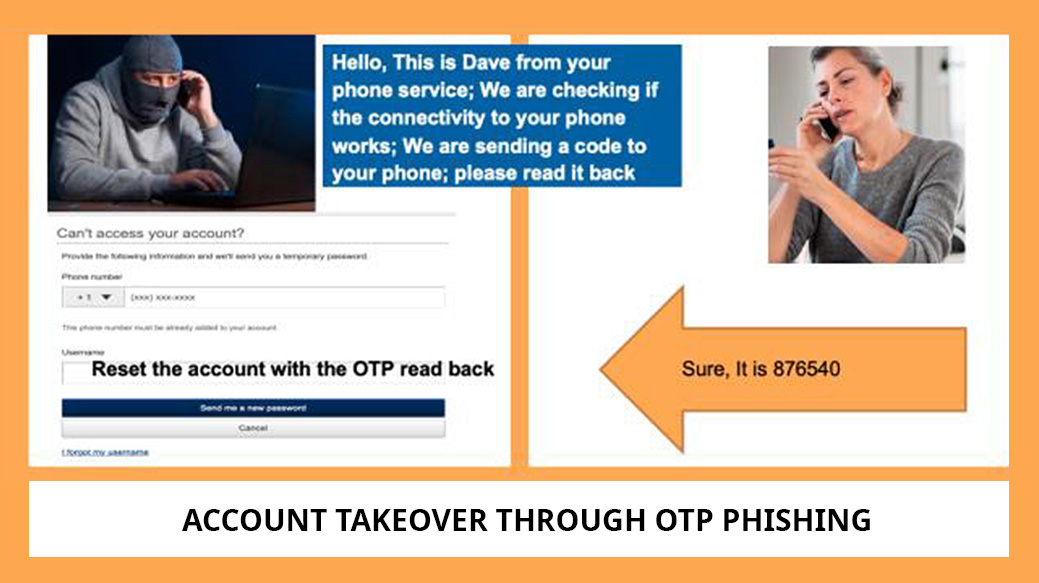
Cloud journey risks more credential exposure: Bearer-aware credentials can easily secure from spoofing
No need for re-registering, with Bearer-aware credentials, when your URLs need to change

Eliminate the risks associated with unwanted credential sharing with Bearer-aware credentials
If your enterprise needs to solve any of the above security gaps along the following, schedule a demo here
- Reduce (in most cases, eliminate) credential leak incident management
- Without substantial capex investment
- Least changes to your applications and infrastructure
- Easy effort-less compliance with FFIEC, HIPAA, CJIS, PCI etc.
- Be in control of authentication verification and not rely on end-user-authentication agents that need certification (adding costs)
- Freedom to migrate and flexibility of login URLs