Credentials denote specific data or authentication tools required to verify the identity of a user, authenticate them and grant access to the enterprise resources. Credentials are extremely important when it comes to securing a company’s network infrastructure, protecting both their employees and customers, and safeguarding their assets.
Once inside the enterprise network, advanced cybercriminals can move laterally, placing backdoors, remote access tools (RATs) and other software to become persistent, exfiltrate the sensitive data for economic gains and making a substantial negative impact on the business aspects.
Before we dive into the credential leaks and their impact, let us look at the SMBs and Enterprises’ journey into cloud adoption. As per Gartner, the cloud adoption has accelerated in the past few years, and by 2023 the following would be the trend
- The public cloud service market is expected to reach $623.3 billion worldwide.
- 83% of enterprise workloads will be in the cloud.
- 94% of enterprises already use a cloud service.
In addition, the SMBs tend to rely heavily on the SaaS products such as Office365 etc. and have a footprint in at least one of the public clouds. The corporate email, confidential data, and business transactions all happen over the cloud.
As per the Anti-Phishing Working Group (APWG), in its Q1 2020 report, the relevant key highlights are as below
- The number of phishing sites detected in the first quarter of 2020 was 165,772, up from the 162,155 observed in the fourth quarter of 2019.
- Phishing that targeted webmail and Software-as-a- Service (SaaS) users continued to be biggest category of phishing.
What does this translate into? The traditional Enterprise perimeter becomes porus and along with mobility, the secure Identity and Access Management (IAM) becomes critical and hence need to pay more attention to the Credential Leaks — be it real-time or otherwise as shown in the below anatomy of threats
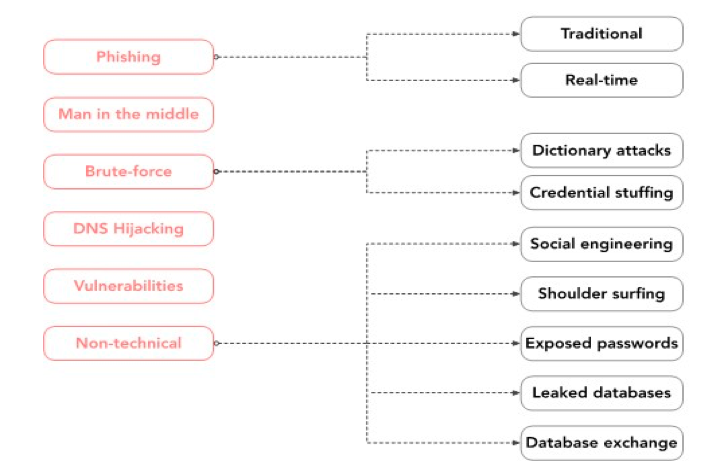
Anatomy of threat vectors leading to credential leaks
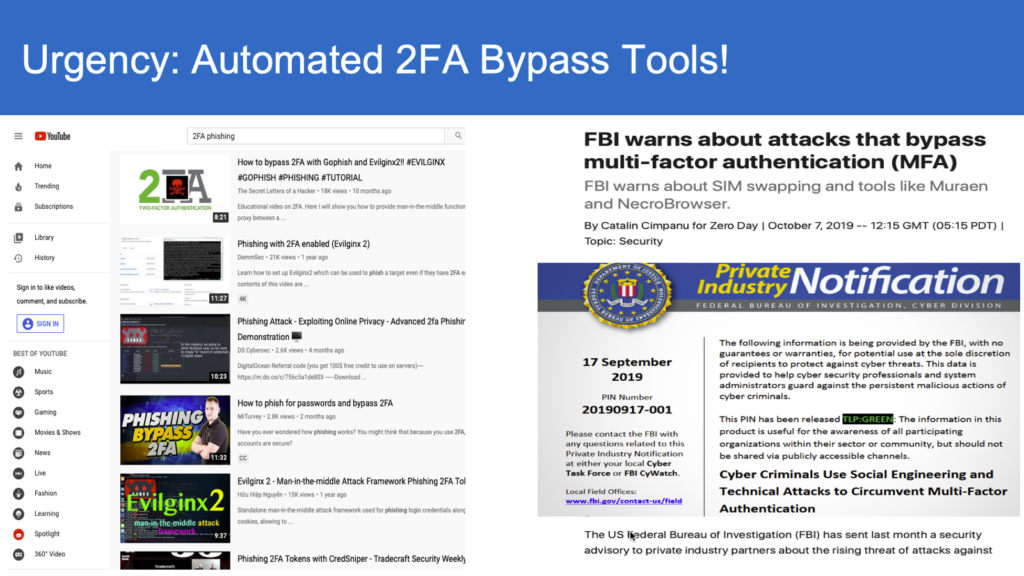
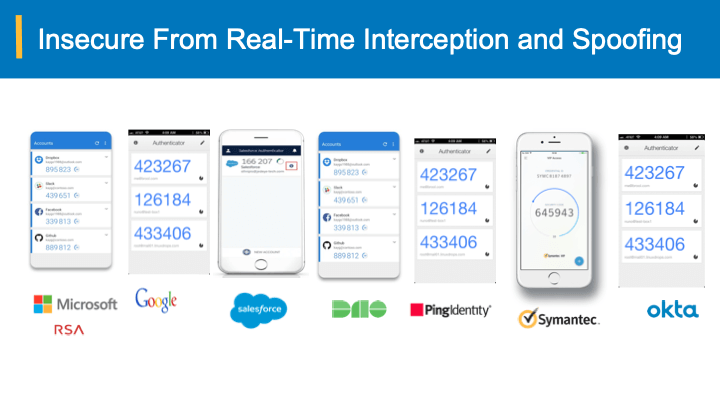
In the context of recent advent of automated tools for proxying and intercepting tools such as Modlishka, EvilNgnx, and Muraena, they have now become mainstream testing tools to bypass widely adopted two-factors schemes such as s/w as well as h/w One-time-Passcodes (OTPs), SMS and out-of-band approvals when it comes to user-authentication.
As noted in our earlier blogs, Passwords and all other popular 2FA schemes are essentially bearer-schemes in the sense that the holder (legitimate user or attacker) can utilize them. This exactly the underlying root cause of so many monitoring and auditing schemes to secure against credential leaks despite spending and securing infrastructure and network/devices.
In contrast, the bearer-sensitive technologies enable the enterprises to secure against such credential leaks. The bearer-sensitive credentials would be tied back to specific users and their devices with watermarks, such that, even if they intercepted and spoofed, the authentication system can detect such spoofing and secure against account take-overs.
For a preview of such mechanisms and their precise benefits, watch our video here.
To schedule a free demo at your convenience, fill out the form or send us an email to info[at]ilogsafe.com