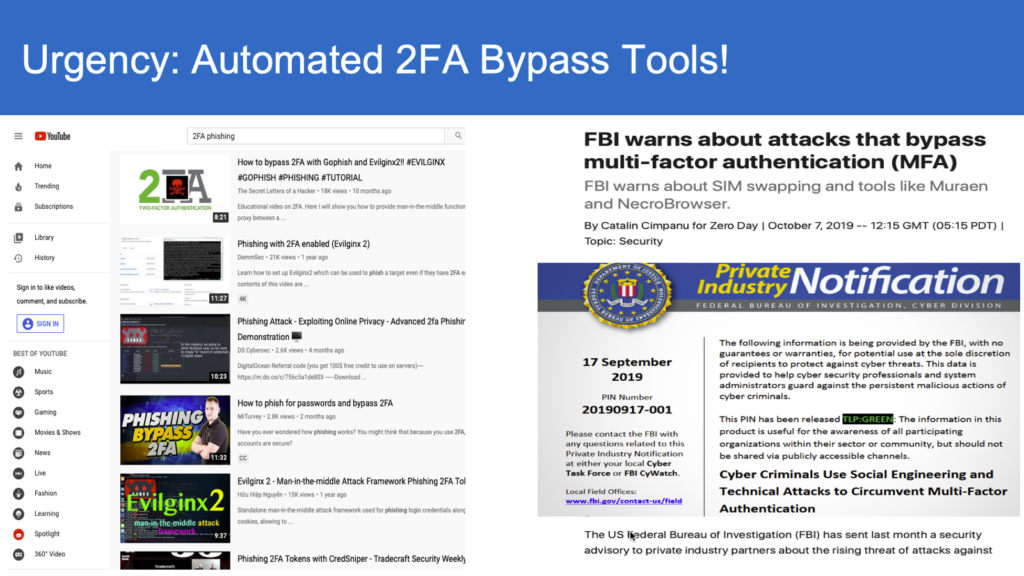
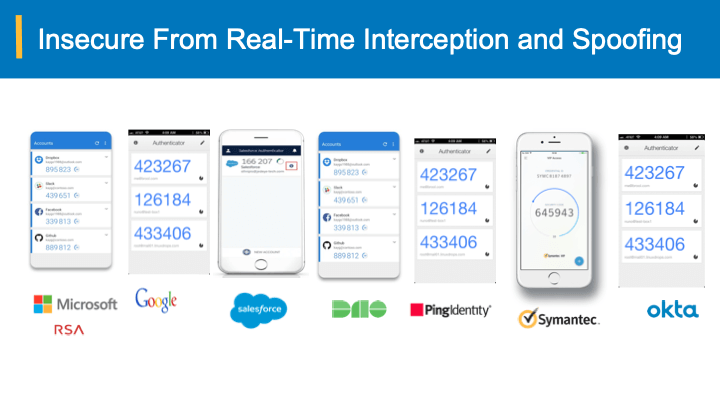
Credential phishing continues to be a growing threat in today’s enterprise. Since the beginning of the COVID-19 pandemic, phishing scams have become more frequent and elaborate. As more businesses and individuals adopt “work-from home” policies, companies fall victim to credential fraud at a much higher rate than ever before.
According to the latest research by Microsoft, the number of phishing attacks has increased 11-fold since February, 2020 when the pandemic first started. By tapping into endpoints, apps, email and company identities, bad actors target all types of enterprises. Affected industries range from the financial sector to healthcare as well as SMBs that rely on SaaS-based technology such as Office 365. As a result, the cost of stolen credentials today has grown 12 percent from 2018 and 72% from 2014. Moreso, dealing with phishing attacks and credential fraud has long-term implications that often last anywhere between 2 to 3 years.
What is Credential Phishing?
Credential phishing attacks take place when bad actors steal company-issued credentials to bypass security measures and gain access to mission-critical data. Phishing, malware and exploits are their go-to tactics in achieving that. By targeting corporate employees and compromising passwords, cybercriminals authenticate applications and ultimately steal data. Once an attacker gets a hold of your login credentials, he or she can easily operate as a valid user inside the network and later sell compromised credentials in the cybercrime underground.
You may think that multi-factor authentication that requires users to validate their identity more than once can be your saving grace, but even this measure is not enough since it can’t be used on every single application employed by your organization. Attackers can also use private keys to gain unauthorized access during the authentication process, so it’s imperative that your IT team is in total control of the authentication and verification process at every network layer.
In recent years, credential phishing attacks became so elaborate, it’s often hard to tell when you’ve been hacked until it’s too late. Sadly, even the use of password managers like LastPass can’t guarantee full protection from credential phishing. You may not suspect anything until you start receiving spam or unsolicited phone calls for unfamiliar services or suddenly realize that you can’t access your accounts and applications.
Let’s take a look at the recent Twitter attack that took place on July 15th, 2020. According to the source, a phone-based social engineering attack allowed cybercriminals to obtain employee credentials, which in turn, led to network and support system infiltration where the ownership of passwords and OTPs was changed. As a result, hackers were able to initiate a payment scam which helped them receive at least $120,000 worth of bitcoins.
“This was a striking reminder of how important each person on our team is in protecting our service,” Twitter said. “We take that responsibility seriously and everyone at Twitter is committed to keeping your information safe.”
How Can Your Company Minimize The Risk of Exposure?
Despite periodic and mandatory training, there is no guarantee your employees will identify phishing attacks to be able to avoid dire consequences similar to what happened with Twitter, successful credential fraud prevention measures have one thing in common: bearer-aware credentials.
Watch this video
Bearer-aware credentials use an authentication process that prevents credentials from changing ownership. This is similar to using traveler’s checks as opposed to cash: a traveler’s check can be assigned only to one person whereas cash can change hands easily. When someone steals your cash, they can use it anywhere. Traveler’s checks are meaningless to criminals since they can only be used by a person to whom they are assigned.
Similarly, bearer-aware credentials prevent hackers from leveraging your passwords because they can be traced back to a specific user and involve an authentication scheme that is unique only to its bearer. Bearer credentials use a device’s digital watermark that’s generated by the server in response to a login request and cannot be replicated nor bypassed by a bad actor.
With bearer-aware credentials in mind, won’t it be nice to have a single form of a robust digital protection to secure your entire network? A solution that’s based on the use of anti-phishing codes that can easily detect interception and prevent credential attacks and account takeovers? Something to give you a peace of mind knowing that there is almost a zero chance for credential theft?
A unique bearer-aware Anti-Spoofing solution is the iLogSafe. Our patented solution uses bearer-aware credentials to eliminate phishing risks that lead to data breaches and fraud. iLogSafe does not alter your existing applications, browsers or infrastructure. It is quantum-safe and customizable to your unique organization.
The benefits of iLogSafe are clear:
- One can actually detect interception and spoofing to shut down the fraudulent sites with iLogSafe
- Reduced reliance on strong passwords and savings from the complex management and resources
- Reduced incident management due to credential exposures, including spear phishing
- Eliminate password management and reduce audit costs
- Better compliance with 2X savings on PCI DSS, HIPAA, FFIEC
- Out-of-box enterprise-grade Single Sign On (SSO) for access to applications and cloud
- Fraud prevention and transactional authentication
- Protected from SIM card swapping
- No constraints on login URLs that users need to register when URLs change – making your merger and acquisition easy
Schedule a quick demo to see how iLogSafe can help you achieve your credential protection goals today!